Eset is the first to document DoubleLocker, a ransomware for Android that takes advantage of the accessibility services of the operating system to encrypt information and block devices.
Eset, the company dedicated to detecting threats, discovered the first ransomware called DoubleLocker that takes advantage of accessibility services for Android. This DoubleLocker can encrypt information and can block the device.
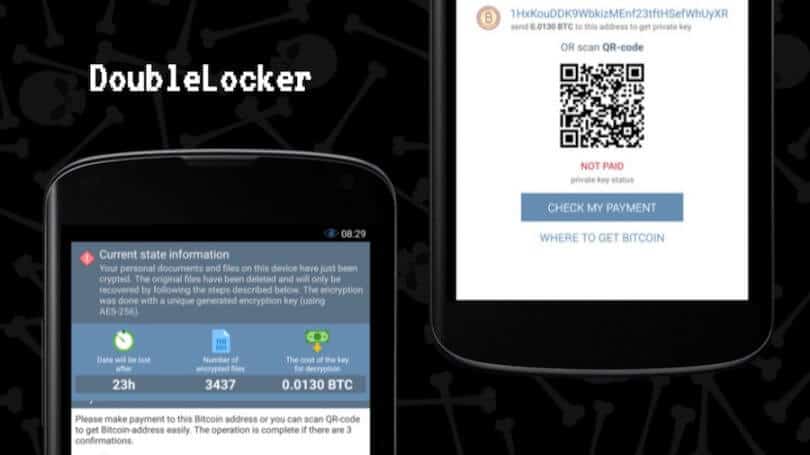
DoubleLocker is the name of the ransomware discovered and comes from the code of a “Banking Trojan” that uses with bad intention the services of accessibility of the mobile operating system of Google, although this DoubleLocker does not have functions related to banking operations or abilities to empty the accounts. This DoubleLocker has tools that allow extortion of the victim since it can change the PIN of the device and it would be impossible to use it again.
“Due to its bank threat roots, DoubleLocker could well become what we can call ransom-bankers. DoubleLocker is a malware that works in two stages. First, this ransomware tries to empty your bank or PayPal account and then lock your device and information to request payment of the ransom. Leaving speculation aside, the first time we saw a trial version of a ransom-banker of this type in the wild was in May 2017, “said Lukas Stefanko, Eset malware researcher who discovered DoubleLocker.
This malware is spread the same as “Banking Trojan”, it is usually distributed through a fake version of Adobe Flash Player, Upload to compromised sites. Once the application is executed, it requests the activation of the malware accessibility service, called “Google Play Service” to deceive users, who may believe that it is a legitimate Google service.
Next, the malware uses those permissions to activate the administrator rights of the computer and establishes itself as the default startup application, in both cases without the user’s consent.
“Establishing yourself as a default startup application (a launcher) is a trick that improves the persistence of malware. Each time the user clicks the Start button, the ransomware is activated and the device locks up again. Thanks to the use of the accessibility service, the user does not know that he executes malware by pressing Start”, explained Lukas Stefanko.
Lukas Stefanko also commented that this is another malware and another reason for users to have security solutions and periodically backup their information.