Introduction:
BeyondCorp is a zero-trust enterprise security model. It allows the employees of the organizations more secure. And they can work from any location. It was built upon the past experience of Google. To know more let us proceed right into this post.
Importance of Network Security
Network security is important because it protects businesses from a wide range of potential threats. With the increasing amount of sensitive data that is stored and transmitted across computer networks, businesses are vulnerable to various cyber-attacks. These attacks vary from malware, phishing, and Ransomware. Further, these types of attacks will result in data loss and reputational damage. In addition, it will result in other financial losses.
Besides, network security is important to ensure the integrity and availability of network resources. A more secure network ensures that authorized users have access to the resources as and when they need it. At the same time secured network prevents unauthorized users from accessing sensitive information. This prevents data breaches and other security incidents that could disrupt business operations.
Network security is a necessary feature of any modern business, regardless of size or industry. By implementing effective network security measures, businesses can protect their data. And the businesses can maintain the trust of their customers and stakeholders. And they can avoid costly security incidents.
The Limitations of Traditional Network Security Models
Traditional network security models have several limitations. Those limitations make them inadequate in today’s business environment. One of the primary limitations is the reliance on perimeter-based security. In perimeter-based security, the focus is on securing the network perimeter. It is to prevent external threats from entering the network. This approach was effective in the past. But it is not sufficient in today’s business environment. It is because; threats can originate from both external and internal sources.
One of the limitations of perimeter-based security is that it assumes that all internal network traffic can be trusted. This is not necessarily the case. Internal threats can be just as dangerous as external ones. For example, if an employee’s device is compromised, that device could potentially access and compromise other network resources. This makes it difficult to ensure the security and integrity of network resources.
Another limitation of traditional network security models is that they often rely on network segmentation to control access to sensitive resources. Segmentation is effective. But it is complex and difficult to manage. This results in gaps in security coverage. And, that can be exploited by attackers.
The traditional network security models are often not designed to handle the complexities of modern business environments, such as remote workforces, cloud-based resources, and mobile devices. Many traditional security models rely on the assumption that all users and resources are located within the organization’s network. But in today’s business environment, users may be accessing resources from remote locations or using cloud-based resources. These make the organizations more difficult to provide effective security coverage for all network resources and users.
To address these limitations, new network security models have emerged. They are such as BeyondCorp. BeyondCorp is a security model developed by Google. And it is designed to provide more comprehensive security coverage than traditional models. Most of the traditional models rely on perimeter-based security. But BeyondCorp is based on the Zero Trust security model. It assumes that all devices and users on the network should be treated as potential threats until they are verified.
BeyondCorp also provides more granular control over user access to network resources. It allows businesses to manage all devices on their network, including those owned by employees. Additionally, BeyondCorp uses contextual data to make access control decisions. That helps to improve security and reduce the risk of data breaches.
The limitations of traditional network security models highlight the need for new, more comprehensive security solutions. By adopting a security model like BeyondCorp, businesses can better protect their data. And they can easily maintain the trust of their customers and stakeholders. In addition, they can avoid many costly security incidents.
Introduction to BeyondCorp as a Solution
BeyondCorp is a security model developed by Google. It aims to provide a more comprehensive and effective approach to network security. Traditional network security models rely on perimeter-based security. And it assumes that all internal network traffic can be trusted. Unlike it, BeyondCorp is based on the Zero Trust security model. It assumes that all devices and users on the network should be treated as potential threats until they are verified.
The Zero Trust security model is based on the principle of “never trust, always verify”. This means that access to network resources is based on several factors. These factors are the user’s identity, the device they are using, the location of the device, and the context of the request. BeyondCorp uses contextual data to make access control decisions. It provides more granular control over user access to network resources. And it helps to improve security and reduce the risk of data breaches.
BeyondCorp also provides several benefits over traditional network security models.
Improved Visibility:
BeyondCorp provides better visibility into the devices and users on the network. It allows businesses to identify potential threats more quickly and accurately.
Greater Flexibility:
It is designed to support modern business environments. The modern business environments are remote workforces, cloud-based resources, and mobile devices. Further, it provides greater flexibility and scalability.
Reduced Complexity:
It simplifies the management of network security by providing a single point of control for access to network resources. A single point of control for access reduces the complexity of managing network segmentation and access control policies.
BeyondCorp represents a significant shift in the approach to network security. In addition, it provides a more effective and comprehensive solution for protecting businesses from cyber threats.
BeyondCorp – The Concept
BeyondCorp is a security model developed by Google. It is designed to provide a more effective and comprehensive approach to network security. The concept behind it is based on the principle of Zero Trust. Zero Trust assumes that all devices and users on the network should be treated as potential threats until they are verified.
Traditional network security models often rely on perimeter-based security. They assume that external threats must be prevented from entering the network. However, this perimeter-based security approach is not sufficient in today’s business environment. Since threats can originate from both external and internal sources.
BeyondCorp takes a different approach to network security by focusing on access control. Access control is based on several factors. The factors are such as the user’s identity, the device they are using, the location of the device, and the context of the request. This Zero Trust approach provides more granular control over user access to network resources. This approach helps to improve security and reduce the risk of data breaches.
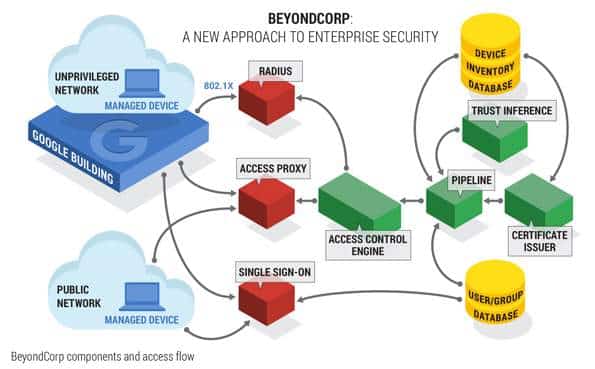
BeyondCorp also provides several benefits over traditional network security models. That includes improved visibility into the devices and users on the network. It provides greater flexibility to support modern business environments. And it reduces complexity in managing network segmentation and access control policies.
The concept behind BeyondCorp represents a significant shift in the approach to network security. It provides a more comprehensive and effective solution for protecting businesses from cyber threats. It adopts the Zero Trust security model and implements access control based on contextual data. Therefore businesses better protect their data. And they maintain the trust of their customers and stakeholders. In addition, they can avoid costly security incidents.
Explanation of BeyondCorp and How It Differs from Traditional Models
BeyondCorp is a security model that provides a more effective and comprehensive approach to network security compared to other traditional security models. The difference between it and traditional models lies in the approach to security.
Traditional security models often rely on perimeter-based security. In Traditional security models, security measures are put in place to protect the network from external threats. However, this approach to traditional security models has several limitations. Since threats can originate from both external and internal sources.
BeyondCorp takes a different approach to network security by focusing on access control. Access control is based on several factors. The factors are such as the user’s identity, the device they are using, the location of the device, and the context of the request. This approach provides more granular control over user access to network resources. And it improves security. Further, it reduces the risk of data breaches.
One of the main differences between BeyondCorp and traditional security models is it uses the Zero Trust security model. The Zero Trust model assumes that all devices and users on the network should be treated as potential threats until they are verified. This means that access to network resources is based on several factors.
Another difference between these security models is that BeyondCorp provides better visibility into the devices and users on the network. This allows businesses to identify potential threats more quickly and accurately. It reduces the risk of security incidents.
It also provides greater flexibility to support modern business environments. Modern business environments are such as remote workforces, cloud-based resources, and mobile devices. This flexibility is essential in today’s business environment. Since most of the employees often work from different locations and devices.
The primary difference between BeyondCorp and traditional security models lies in the approach to security. It focuses on access control and uses contextual data to make access control decisions. In addition, it provides a more comprehensive and effective solution for protecting businesses from cyber threats.
Overview of the Zero Trust Security Model and Its Role in BeyondCorp
The Zero Trust security model is a security concept that assumes that all devices and users on a network should be treated as potential threats until they are verified. In other words, Zero Trust assumes that no user or device should be automatically trusted based on their location or other characteristics.
The Zero Trust model is based on the principle of “never trust, always verify”. This means that access to network resources is based on several factors. The factors are such as the user’s identity, the device they are using, the location of the device, and the context of the request. By using contextual data to make access control decisions, Zero Trust provides more granular control over user access to network resources. It improves security. And further, it reduces the risk of data breaches.
As we already discussed, BeyondCorp is built on the Zero Trust security model. It means that it assumes that no device or user on the network can be trusted until they are verified. It uses several factors to determine whether to grant access to network resources. The role of the Zero Trust security model in BeyondCorp is to provide a more comprehensive and effective approach to network security. Zero Trust security model plays a critical role in it.
This security model provides a foundation for the access control mechanisms. These access control mechanisms are used to secure network resources. It adopts the Zero Trust model and implements access control based on contextual data. Further, it provides a more effective and comprehensive solution for protecting businesses from cyber threats.
Key Components of Beyondcorp
BeyondCorp is a security model that is built on the principle of Zero Trust. And it focuses on providing access control to network resources based on several factors. There are several key components of it, they are:
Identity and Access Management (IAM)-
Identity and Access Management is a critical component of BeyondCorp. It provides a framework for managing user identities and authenticating users. And it authorizes access to network resources. IAM helps to ensure that only authorized users can access network resources. In BeyondCorp, IAM is implemented through several mechanisms.
Those mechanisms are:
Multi-Factor Authentication- Multi-factor authentication is used to verify a user’s identity before granting access to network resources. This typically involves requiring users to provide something they know, such as a password. And something they have, such as a token or a biometric factor like a fingerprint or face scanning.
Role-Based Access Control- Role-based access control (RBAC) is used to determine what network resources a user is allowed to access. It is based on their job responsibilities and permissions. RBAC helps to ensure that users only have access to the resources they need to do their job.
Attribute-Based Access Control- Attribute-based access control (ABAC) is used to determine what network resources a user is permitted to access based on their attributes. The resources are such as their department, location, or device type. ABAC provides more granular control over access to network resources than RBAC.
Device and Network Security-
This security model also includes device and network security measures to protect network resources from unauthorized access and other threats.
Some of the key components of device and network security in BeyondCorp are:
Encryption- Encryption is used to protect data in transit and at rest. All data transmitted over the network is encrypted using secure protocols such as TLS. While data stored on devices or in the cloud is encrypted at rest using encryption algorithms such as AES.
Firewalls- Firewalls are used to control access to network resources. They are typically configured to allow only authorized traffic to pass through and block all other traffic.
Intrusion Detection and Prevention Systems (IDPS)- Intrusion detection and prevention systems are used to detect and block malicious activity on the network. They monitor network traffic for suspicious behavior. And they take action to block or isolate malicious traffic.
Context-Aware Access Control-
Context-aware access control is a key feature of it. It uses contextual data to make access control decisions. The contextual data are such as the user’s identity, the device they are using, and the location of the device. This contextual data helps to provide more granular control over access to network resources. It reduces the risk of unauthorized access. Context-aware access control is implemented through several mechanisms.
Device Posture Assessment- Device posture assessment is used to evaluate the security posture of devices before granting access to network resources. This involves checking for security updates, anti-virus software, and other security measures.
Geographic Location- Geographic location is used to determine whether a user’s location is consistent with their expected location. If a user’s location is unexpected or suspicious, access to network resources is denied.
Time of Day- Time of day is used to determine whether a user’s access request is consistent with their usual behavior. For example, if a user typically accesses network resources during business hours but suddenly requests access at midnight, then this may trigger a security alert.
Cloud-Based Infrastructure-
BeyondCorp leverages cloud-based infrastructure to provide better scalability and flexibility. The cloud-based infrastructure allows it to easily accommodate remote workforces, mobile devices, and cloud-based resources. It also provides better visibility and control over network resources. Since all network activity is centralized in the cloud, it is easily achieved. Some of the key components of cloud-based infrastructure in BeyondCorp include:
Cloud-Based Directory Services- Cloud-based directory services such as Azure Active Directory or Google Cloud Identity are used to manage user identities, authentication, and authorization.
Cloud-Based Application Hosting- Cloud-based application hosting platforms such as Google Cloud Platform or Microsoft Azure are used to host and manage network resources, and applications.
Continuous Monitoring-
Continuous monitoring is an essential component of BeyondCorp. An, Continuous monitoring involves the ongoing monitoring and analysis of network activity to detect and respond to security threats in real-time. This allows organizations to quickly identify and respond to security incidents. It reduces the risk of data breaches and other cyber attacks.
The continuous monitoring is implemented through several mechanisms, including:
Network Traffic Analysis- Network traffic analysis involves monitoring network traffic to detect suspicious activity and anomalies. It is monitoring for unusual patterns of traffic, unexpected ports, and protocols. And, also for any unauthorized access attempts that may happen.
Endpoint Monitoring- Endpoint monitoring involves monitoring the security posture of devices connected to the network. This includes monitoring for security updates, anti-virus software, and other security measures.
User Behavior Analytics- User behavior analytics involves analyzing user behavior to detect anomalous activity, such as unusual login patterns, access attempts outside of normal business hours, and attempts to access unauthorized resources.
Continuous monitoring is an important component of it. And it allows organizations to quickly identify and respond to security incidents. It improves overall network security by providing ongoing visibility into network activity. It enables organizations to proactively identify and address potential security issues before they become serious threats.
The key components work together to provide a more comprehensive and effective approach to network security. It provides better visibility and control over network resources. In addition, it is helping organizations to reduce the risk of cyber threats.
How BeyondCorp Improves Network Security
It improves network security in several ways:
Zero Trust Security Model:
Traditional network security models rely on a perimeter-based approach. The network is secured by a firewall in the traditional approach. All users and devices within the perimeter are assumed to be trusted. However, this approach is no longer effective in today’s increasingly mobile and cloud-based world. Today users and devices can access resources from anywhere.
BeyondCorp’s zero trust security models assume that all devices and users are untrusted until proven otherwise. This means that access to resources is granted on a need-to-know basis. And all access requests are continuously evaluated based on a variety of factors such as device health, user identity, and network context. Implementing this model ensures that only authorized users and devices are granted access to resources. And this zero trust security model reduces the risk of unauthorized access and data breaches.
Device Health Checks:
BeyondCorp requires that all devices connecting to the network undergo health checks so that they meet the organization’s security standards. This includes verifying that the device is up-to-date with security patches and antivirus software. And that it meets other security requirements. Devices that fail to meet these standards are not granted access to network resources until they are brought up to standard. This prevents compromised devices from accessing sensitive data and resources. This type of protocol reduces the risk of data breaches and other cyber attacks.
Continuous Monitoring:
BeyondCorp continuously monitors network activity to detect and respond to security threats in real-time. This monitors network traffic for unusual activity and analyzes user behavior to detect anomalous activity. It provides ongoing visibility into network activity. It helps organizations quickly identify and respond to security incidents. Thereby it reduces the risk of data breaches and other cyber attacks.
Access Controls:
It uses granular access controls to ensure that users only have access to the resources they need to perform their job functions. This reduces the risk of accidental or intentional data breaches by limiting the exposure of sensitive data. Access controls are based on a variety of factors, including user identity, device health, and network context. Besides, they are continuously evaluated to ensure that users only have access to the resources they need, when they need them.
Overall, it improves network security by implementing a zero trust security model. It does device health checks. In addition, it provides continuous monitoring. Further, it uses granular access controls to limit the exposure of sensitive data. By implementing these measures, it reduces the risk of data breaches and other cyber attacks. It helps organizations to protect their sensitive data. And it maintains the trust of its customers and stakeholders.
How to Address Common Network Security Challenges with BeyondCorp
It is designed to address many of the common network security challenges that organizations face. Here are some examples of how BeyondCorp can help address these challenges:
Phishing Attacks
Phishing attacks are a common tactic used by cybercriminals to trick users. The hackers trick the users and get them into divulging sensitive information or installing malware. Its zero trust security models prevent these attacks by requiring multi-factor authentication (MFA) for all access requests. This means that even if an attacker obtains a user’s credentials through a phishing attack, they could not gain access. They would still need to provide a second factor of authentication to gain access to network resources. Additionally, its continuous monitoring detects unusual access patterns that may indicate a compromised account. It enables organizations to take action to prevent a breach.
Malware and Ransomware
Malware and Ransomware are often spread through infected devices that are granted access to network resources. BeyondCorp’s device health checks prevent these attacks. The device health checks ensure that all devices connecting to the network are up-to-date with security patches and antivirus software. Any device is found to be infected with malware. Then it will be quarantined. And it is prevented from accessing network resources until it is cleaned.
Insider Threats
Insider threats are a major concern for many organizations. Since employees with authorized access to sensitive data pose a significant risk. Its granular access controls can mitigate this risk by ensuring that employees only have access to the resources they need to perform their job functions. Additionally, its continuous monitoring detects unusual access patterns that may indicate an insider threat. Thereby it enables organizations to take action to prevent a breach.
Third-Party Access
Many organizations need to grant third-party vendors and contractors access to network resources. That poses a security risk. BeyondCorp’s zero trust security model mitigates this risk by requiring that all third-party access requests go through the same authentication and access control processes as internal users. This means that third-party users are subject to the same security standards as internal users. It reduces the risk of a data breach.
By addressing these common network security challenges, BeyondCorp helps organizations to improve their overall security posture. and it reduces the risk of a data breach or cyber attack. It’s important to note that no security solution is foolproof. And organizations should always implement a multi-layered approach to security that includes people, processes, and technology.
Device Security and Access Control with BeyondCorp
The Device security and access control are two key components of BeyondCorp’s zero trust security models.
Device security
In today’s world, the rise of remote work and the use of personal devices for work purposes increases many folds. Therefore it is more important than ever to ensure that devices connecting to the network are secure. BeyondCorp addresses this issue. It requires that all devices connecting to the network meet minimum security standards.
The minimum standards are such as having up-to-date security patches and antivirus software. This is accomplished through device health checks. These checks are performed each time a device attempts to connect to the network. A device found to be non-compliant with these standards will be quarantined or denied access to network resources until it is brought up to date. This prevents the spread of malware and other security threats.
Access Control:
Access control is another critical component of BeyondCorp’s zero trust security models. By using granular access controls, BeyondCorp ensures that users only have access to the resources they need to perform their job functions. This is accomplished through the use of policies that define what resources each user or group of users can access. These policies are based on a variety of factors. The factors are, such as the user’s role in the organization, the sensitivity of the data being accessed, and the device being used to access the data. By limiting access to sensitive data, BeyondCorp prevents unauthorized access and reduces the risk of data breaches.
Multi-Factor Authentication (MFA)
In addition to these measures, BeyondCorp also includes multi-factor authentication (MFA) for all access requests. This means that users must provide a second factor of authentication in addition to their username and password, such as a code sent to their mobile device or a biometric scan. This prevents unauthorized access if a user’s credentials are compromised. MFA is an important security measure that is common in the industry, as it adds an extra layer of security to the authentication process.
Device security and access control are critical components of BeyondCorp’s zero trust security models. By ensuring that devices meet minimum security standards and that those users only have access to the resources they need. BeyondCorp reduces the risk of data breaches and other security threats. With the rise of remote work and the use of personal devices for work purposes, it’s more important than ever to have a strong security posture. BeyondCorp provides a comprehensive solution for organizations looking to improve their security posture and reduce the risk of a data breach or cyber attack.
The Importance of Identity Management in BeyondCorp
Identity management is a crucial aspect of BeyondCorp’s zero trust security models. With the rise of cloud computing, remote work, and mobile devices, traditional perimeter-based security models are no longer sufficient to protect against cyber attacks. Instead, organizations need to focus on identity-based security. That means that users and devices are granted access to resources based on their identity and context.
In this security model, identity management is used to ensure that users have the appropriate permissions to access the resources they need to perform their job functions. This is accomplished through the use of identity providers. Identity Providers are responsible for verifying a user’s identity and providing authentication credentials. It supports a variety of identity providers such as Google accounts, Active Directory, and OAuth 2.0, which are a few.
Once a user has been authenticated, BeyondCorp uses access control policies to determine what resources the user can access. These policies are based on the user’s identity. And also; based on contextual information such as the device being used to access the resource, the location of the user, and the sensitivity of the data being accessed. By using granular access controls, BeyondCorp ensures that users only have access to the resources they need to perform their job functions. It reduces the risk of unauthorized access.
Identity management is important for device security in BeyondCorp. When a device attempts to connect to the network, it must first be authenticated and authorized. This is accomplished through the use of device certificates. They are issued by the organization’s identity provider. These certificates are used to verify that the device is authorized to connect to the network. And they ensure that the device meets minimum security standards, such as having up-to-date security patches and antivirus software.
In addition to these measures, BeyondCorp also supports multi-factor authentication (MFA) for all access requests. This means that users must provide a second factor of authentication in addition to their username and password, such as a code sent to their mobile device or a biometric scan. MFA is an important security measure. And it helps to prevent unauthorized access in the event that a user’s credentials are compromised.
Overall, identity management is a critical component of BeyondCorp’s zero trust security models. By focusing on identity-based security, it reduces the risk of data breaches and other security threats. And it ensures users and devices are authenticated and authorized before being granted access to resources. With the rise of cloud computing, remote work, and mobile devices, identity management has become more important than ever for organizations looking to improve their security posture and protect against cyber attacks.
Real-World Examples of Businesses Benefiting from Beyondcorp
Several businesses have reported significant improvements in their security posture and operational efficiency after adopting BeyondCorp. Here are a few examples:
Google –
As mentioned earlier, Google is the originator of the BeyondCorp concept. Google has been using this security solution to protect its internal network for several years now. The company has stated that BeyondCorp has helped them to reduce their reliance on VPNs and other legacy security solutions. It results in improved visibility and controls over access to their network resources. Google’s experience with BeyondCorp has been one of the driving forces behind the growing interest in this security model.
Dropbox –
As a cloud-based platform that enables collaboration across different devices and networks, Dropbox has unique security challenges that require a modern security solution. After adopting BeyondCorp, Dropbox has reported improved visibility into access requests. It reduced the time required to provision new access. By shifting its security model to a zero trust, identity-based approach, Dropbox has been able to improve their overall security posture. Also, this security model makes it easier for their employees to work remotely.
PwC –
PwC is a global professional services firm that serves clients across various industries. In addition, PwC have a distributed workforce and a wide range of devices and applications in use. Besides, PwC needed a modern security solution that could provide visibility and control over access to their network resources. After adopting BeyondCorp, PwC has been able to reduce their attack surface. And they improved their ability to detect and respond to security incidents. The company has reported that BeyondCorp has helped them to achieve their security objectives. And also it enables their employees to work remotely from any device.
Coca-Cola –
It is a global brand with a large workforce spread across different locations. Coca-Cola needed a security solution that could provide secure access to their network resources from any location or device. After adopting BeyondCorp, Coca-Cola was able to implement the solution in just three months. It results in improved visibility into access requests and reduced time to provision new access. This security solution has enabled Coca-Cola to achieve their security objectives. And also it provides a seamless user experience for their employees.
These real-world examples illustrate the benefits of adopting a modern security model like BeyondCorp. By shifting the focus from network security to identity-based security and zero trust principles, BeyondCorp helps organizations to reduce their attack surface and improve their ability to detect and respond to security incidents. This approach is especially important in today’s remote work environment. In a remote work environment, employees need to access network resources from different locations and devices. BeyondCorp provides a scalable and flexible security solution. That solution enables organizations to achieve their security objectives. And also it enables their employees to work efficiently and securely.
BeyondCorp and Google
Google is often synonymous with BeyondCorp. Google developed that security model. And it has been using it for several years to protect its internal network. In fact, BeyondCorp was developed by Google’s security team as a response to their dissatisfaction with traditional network security models. Traditional network securities relied heavily on perimeter-based security. They assumed trust in internal devices.
Google’s implementation of BeyondCorp involves a comprehensive identity and access management system. It grants access based on the user’s identity and the device they are using. Access is granted on a need-to-know basis. And all devices are treated as untrusted until they are verified and authenticated. This eliminates the need for traditional network perimeter security measures such as VPNs, firewalls, and network segmentation.
Google has reported numerous benefits from adopting BeyondCorp. Those benefits include improved visibility and control over access requests, reduced reliance on VPNs, and improved incident response times. Additionally, it has enabled Google to provide a more seamless user experience for their employees. It allows them to access network resources from any location and device.
As the originator of the BeyondCorp concept, Google’s implementation serves as a blueprint for other organizations looking to adopt the security model. Google has also made the code for their BeyondCorp implementation as open source. Making it as an open source allows other organizations to leverage and customize the security solution for their own needs.
Google’s Implementation of BeyondCorp
Google’s implementation of BeyondCorp is considered one of the most comprehensive and successful examples of the security model in action. The approach involves a range of security technologies and protocols that work together to provide a layered and dynamic security posture. Google uses a variety of tools and technologies to create a multi-layered security approach
Identity and Access Management (IAM) System-
At the heart of Google’s BeyondCorp implementation is their Identity and Access Management (IAM) system. This system manages user identities and access to Google’s network resources. And this system is responsible for assigning roles to users. And that system determines what resources they can access and what actions they can perform.
Endpoint Verification
Endpoint verification is another key component of Google’s BeyondCorp strategy. This technology ensures that all devices accessing the network meet certain security requirements before they are granted access. The verifying of devices are running the latest software updates and they have up-to-date security settings. This helps to prevent compromised or vulnerable devices from accessing the network.
Context-Aware Access
Google’s context-aware access technology is also a critical part of their BeyondCorp approach. This technology takes into account various factors. These factors are the user’s location, device type, and network connection when determining whether or not to grant access to a resource. This helps to prevent unauthorized access attempts from unknown devices or locations.
Security Analytics
To monitor network traffic for potential security threats, Google uses a range of security analytics tools. These tools continuously analyze network traffic for suspicious behavior and potential security incidents. This enables Google’s security team to quickly detect and respond to security incidents before they can cause damage.
Overall, Google’s BeyondCorp implementation has enabled the company to improve its security posture significantly. This security model moves away from traditional perimeter-based security models and towards a more identity-centric approach. Google has been able to gain better visibility and control over access requests. It reduces their reliance on VPNs and improves incident response times. The approach has also allowed employees to access network resources from any location and device, providing a more seamless user experience.
As a result of the success of Google’s implementation of BeyondCorp, other organizations have taken notice and begun to adopt the security model for their own networks. Google has also made the code for their BeyondCorp implementation open source, which allows other organizations to leverage and customize the security solution for their own needs.
Differences in Google’s Implementation Compared to Other Businesses
Google’s implementation of BeyondCorp differs from other businesses in many ways.
First, Google’s security approach is highly customized to their own unique needs and infrastructure. Google has a massive and complex network with a wide variety of resources that need to be secured. They have invested heavily in developing their own tools and technologies to support their BeyondCorp implementation.
Second, Google’s security approach is incredibly data-driven. Google collects and analyzes vast amounts of data on their network traffic and user behavior. It uses this information to continually refine and improve their security posture. This data-driven approach allows Google to quickly detect and respond to security threats. And they adapt their security policies in real-time as needed.
Third, Google’s approach is highly automated. Google has developed a range of automated tools and processes that help to streamline security operations. These automated tools reduce the risk of human error. These tools automatically provision and de-provision user access. And it automatically detects and responds to security incidents. In addition, it automates compliance monitoring and reporting.
Finally, Google’s security approach is highly transparent. Google provides detailed documentation. And they provide public presentations on their security practices and technologies. They have even open-sourced much of their BeyondCorp code. This level of transparency helps to build trust with both internal stakeholders and external customers and partners. Further, it helps to demonstrate Google’s commitment to security and privacy.
Now a day, many organizations have adopted the BeyondCorp security model. Google’s implementation stands out for its customization, data-driven approach, automation, and transparency.
Insights into How Google Continues to Improve BeyondCorp
Google’s implementation of BeyondCorp is considered to be one of the most successful and mature implementations of the model. It has been in use at Google for over a decade. It has proven to be an effective solution for securing their infrastructure and data.
Expanding Access Management Capabilities
The differences between Google’s implementation of this security model and that of other models are the scalability and complexity of their infrastructure. Google is one of the largest networks. And it is the most complex network in the world. It has thousands of servers and data centers. And they are spread across the globe. This requires a high degree of automation and orchestration to ensure that security policies are enforced consistently and efficiently.
Enhancing Visibility and Monitoring
Google’s implementation of the security model emphasizes the use of context-aware access controls. This means that access to resources is based on several factors. These factors are the user’s identity, user’s device, their location, and other contextual factors. It allows for a more fine-grained approach to security. It prevents unauthorized access from compromised devices or networks.
Integrating With Other Google Security Services
In addition, Google places a strong emphasis on automation and machine learning when it comes to security. They have developed a number of tools and processes that use machine learning algorithms. These tools detect anomalous behavior and potential security threats. This allows them to respond quickly and effectively to security incidents. And these tools minimize the impact of any potential breaches.
Providing More Customization Options
Google also provides a range of customization options for the implementation of its security model. This allows organizations to tailor the security model to their specific needs and infrastructure. And that security model ensures that the model remains flexible and adaptable to evolving threats.
Google’s implementation of BeyondCorp is a testament to the effectiveness of the model as a security solution for large and complex organizations. Google has created a state-of-the-art security solution that continues to evolve and improve over time.
Is Beyondcorp Right for Your Business?
Implementing BeyondCorp in your business depends on a variety of factors. They are the size of your organization, the complexity of your infrastructure, and your security requirements.
One of the benefits of it is its ability to provide a zero-trust security model. This security model improves security by requiring continuous authentication and authorization for all access to resources. This is particularly important for organizations that handle sensitive data or have a large number of remote workers. It prevents unauthorized access. And it reduces the risk of data breaches.
However, implementing it is a complex and resource-intensive process. Particularly it is tough for larger organizations with a diverse set of users and devices. It requires a significant investment in both time and resources to properly configure and maintain the necessary infrastructure. And it requires additional staffing and training for IT and security teams.
Additionally, it is an effective solution for many organizations. But it is not a one-size-fits-all solution. Some organizations may have unique security requirements or regulatory compliance needs that may not be fully addressed by the model.
Before deciding whether or not to implement BeyondCorp, it is important to carefully consider your organization’s specific security needs and requirements. And also the potential benefits and drawbacks of the model. Consulting with a security expert or trusted vendor needs to determine the right fit for your business.
Factors to Consider When Evaluating BeyondCorp
When considering BeyondCorp as s security solution for your business, it is important to carefully evaluate several factors to ensure it aligns with your organization’s needs and requirements.
Security Requirements
First, the organization needs to consider and evaluate its security requirements. This security model is designed to provide strong security controls and continuous monitoring. It is particularly important for organizations that handle sensitive data or assets. If your organization does not need any high level of security requirements, then it is not necessary to implement it.
Infrastructure Complexity
Next, you should evaluate the complexity of your infrastructure. This security model requires a significant investment in time and resources. Then only it can be properly configured and maintained with the necessary infrastructure. Consider whether your organization has the technical expertise. And it has additional resources to manage this complex infrastructure.
User and Device Management
User and device management is also an important factor to consider. BeyondCorp relies on a user and device-centric security model. It requires changes to your organization’s existing processes and resources. Check whether your organization has the necessary resources. And it can processes in place to manage users and devices in this way.
Regulatory Compliance:
Regulatory compliance is also an important consideration. If your organization needs to comply with regulatory standards such as HIPAA, PCI-DSS, or GDPR, it is important to evaluate whether this security model meets these requirements.
Cost
Cost is also an important consideration when evaluating this security model. Implementing BeyondCorp needs significant investment in both time and resources. That includes infrastructure, personnel, and ongoing maintenance. Find out if your organization has the budget and resources to support the necessary infrastructure and ongoing maintenance.
Scalability
Scalability is one of the important factors to consider. It is designed to be a scalable solution that can grow with your organization. Check whether you can scale it to meet your organization’s future needs.
User Experience
Finally, user experience is an important consideration, particularly for remote workers who may need to access resources from multiple devices or locations. BeyondCorp impacts the user experience, so it is important to evaluate how BeyondCorp may impact the user experience and whether this is acceptable for your organization.
Evaluating BeyondCorp requires careful consideration of your organization’s specific needs and requirements. Consulting with a security expert or trusted vendor helps determine whether BeyondCorp is the right fit for your business.
Potential Challenges and Drawbacks
While BeyondCorp offers significant benefits in terms of network security. There are also potential challenges and drawbacks to consider when implementing this solution.
Complexity
One potential challenge is the complexity of the infrastructure required to support BeyondCorp. Implementing it requires significant investment in time and resources to properly configure and maintain the necessary infrastructure. Implementing this model includes identity and access management, and implementing secure device management. It also implements continuous monitoring and security controls. This is particularly challenging for smaller organizations with limited resources.
Impact on User Experience
Another potential challenge is the impact on user experience. This security model relies on a user and device-centric security model. It requires changes to your organization’s existing processes and resources. This will impact the user experience and may require additional training for employees.
Regulatory Compliance
Regulatory compliance is also an important consideration. Most organizations must comply with regulatory standards such as HIPAA, PCI-DSS, or GDPR. Therefore it is important to evaluate whether BeyondCorp meets these requirements.
Cost
Cost is another important consideration when evaluating BeyondCorp. Implementing BeyondCorp needs a significant investment in both time and resources, including infrastructure, personnel, and ongoing maintenance. Consider whether your organization has the budget and resources to support the necessary infrastructure and ongoing maintenance.
Single Point Failure:
Finally, there is a risk that BeyondCorp can create a single point of failure. All user access is controlled through a central identity provider. If this system fails or is breached, it will have a significant impact on your organization’s security posture. It is important to consider strategies to mitigate this risk. This risk can be mitigated by implementing redundant systems or regularly backing up critical data.
It is important to carefully evaluate the potential challenges and drawbacks of implementing it. And need to determine whether these outweigh the benefits for your organization. Consulting with a security expert or trusted vendor will help determine whether it is the right fit for your business.
Recommendations for businesses considering BeyondCorp
Let you start with a thorough assessment of your organization’s security needs and existing infrastructure:
Before implementing this security model, it’s important to understand and check your organization’s current security posture. And need to identify any gaps or vulnerabilities that need to be addressed. This involves conducting a security audit or risk assessment to evaluate your organization’s existing security controls and identify areas of weakness. You need to consider your organization’s specific security needs. These security needs may be such as regulatory compliance requirements or the need to protect sensitive data.
Develop A Comprehensive Implementation Plan:
Once you understand the organization’s security needs and infrastructure, you need to develop a comprehensive implementation plan. That comprehensive implementation plan should outline the steps needed to deploy the security model. This plan includes a clear roadmap for deployment, testing, and ongoing maintenance. And you need to train employees on new processes and technologies. It’s important to ensure that the implementation plan is aligned with your organization’s business objectives. and it must include provisions for contingency planning in case of unexpected issues or delays.
Invest In The Necessary Infrastructure And Personnel To Support BeyondCorp:
Implementing BeyondCorp requires significant investment in infrastructure and personnel. This involves implementing identity and access management systems, secure device management, and continuous monitoring and security controls. It also involves hiring additional personnel with expertise in these areas. Investing in the right tools and personnel ensures successful implementation and ongoing maintenance.
Consider Partnering With A Trusted Vendor Or Security Expert:
Partnering with a trusted vendor or security expert organization provides access to specialized expertise and resources that are not available in-house. This is particularly helpful if your organization does not have the necessary personnel or expertise to implement this security model on its own. While selecting a vendor or expert, it’s important to ensure that they have a strong track record of implementing it. It provides ongoing support and maintenance as needed.
Prioritize User Experience Throughout The Implementation Process:
Implementing this security model involves significant changes to existing processes and resources. It impacts employee productivity and satisfaction. To ensure a successful implementation, it’s important to prioritize user experience throughout the process. This involves communicating with employees about changes to existing processes and resources. And they need to provide training and support as needed. And they need to ensure that security measures do not unduly impact productivity. By prioritizing user experience, organizations ensure a smoother transition to this security model. It reduces the risk of resistance or pushback from employees.
Regularly Review And Update Your Beyondcorp Implementation:
BeyondCorp is not a one-time implementation. But it is rather an ongoing process that requires regular review and updating. This involves conducting regular security assessments to identify new threats or vulnerabilities. Organizations need to implement new security measures as needed. And they need to keep them up-to-date with best practices and emerging threats. By regularly reviewing and updating BeyondCorp implementation, organizations ensure that they meet evolving security needs.
Implementing BeyondCorp is a complex and resource-intensive process. At the same time but it offers significant benefits in terms of network security. Businesses need to evaluate carefully their needs. Then they need to develop a comprehensive implementation plan. In addition, businesses have to prioritize the user experience and ongoing maintenance. Then businesses can successfully implement BeyondCorp and improve your organization’s overall security posture.
Summary of the Key Points:
Sure, here’s a summary of the key points discussed in this chat about BeyondCorp:
Network security is critical for businesses, but traditional security models have limitations, such as inadequate access control and difficulty enforcing policies.
BeyondCorp is a security framework developed by Google. It is based on a zero-trust model. And it is designed to address these limitations.
The key components of this model include identity management, device security, network security, and access control.
It improves network security by shifting the focus from network location to user identity and device security. In addition, it enables continuous monitoring. Further, it reduces the risk of data breaches.
Businesses considering this security model should evaluate factors such as their existing infrastructure, budget, and security needs. And also the business needs to evaluate the potential challenges such as implementation complexity and user adoption.
Businesses can benefit from BeyondCorp by improving network security. It reduces the risk of data breaches. It enables flexible access control policies. But they should also carefully evaluate the framework and ensure it aligns with their security needs and goals.
Reinforcement of The Importance of Network Security and The Limitations of Traditional Models
Here follows potential reinforcement of the importance of network security and the limitations of traditional models:
Network security is one of the most critical concerns for businesses of all sizes. Businesses rely on their networks to store sensitive data, in today’s digital world. They use the network to communicate with clients, and conduct transactions. Therefore, securing these networks is essential to protect them against potential cyberattacks. Protecting their networks helps them to avoid data breaches and other security threats.
Unfortunately, traditional network security models have limitations that make them insufficient in today’s complex threat landscape. These models often focus on securing the perimeter of the network, assuming that all devices within it are trustworthy. However, this approach has several limitations. For example, it can be challenging to enforce access control policies and monitor network activity effectively, especially as employees and contractors access networks from various locations and devices.
Furthermore, traditional network security models may rely on outdated or insecure protocols and technology, making them vulnerable to emerging cyber threats. This vulnerability can lead to significant data breaches that compromise the privacy and security of the business and its clients.
Given these limitations, businesses need to adopt new security models that can adapt to the changing threat landscape. BeyondCorp is one such security framework that offers a more flexible, scalable, and secure approach to network security. By shifting the focus from network location to user identity and device security, BeyondCorp enables continuous monitoring and reduces the risk of data breaches.
Encouragement for Businesses to Consider Beyondcorp as a Solution
Certainly, there’s a potential encouragement for businesses to consider BeyondCorp as a solution:
Your business may struggle with the limitations of traditional network security models. Then it may be time to consider a more flexible and adaptive security framework. BeyondCorp offers a cutting-edge solution that prioritizes user identity and device security over network location. It enables businesses to better manage access control policies and monitor network activity.
Its Zero Trust security model is designed to provide continuous protection against potential cyber threats. That protection is regardless of where employees and contractors access the network. By implementing it, businesses establish a more secure and scalable network infrastructure. And that adapts to the changing threat landscape.
Google’s implementation of this security model provides a real-world example of the framework’s effectiveness. And Google is reporting significant improvements in security and productivity. With its use, Google has been able to provide its employees with secure access to sensitive data from anywhere in the world, without compromising security.
If you’re considering adopting BeyondCorp, it’s essential to evaluate your business’s unique needs and challenges to determine whether it’s the right solution for you. If you’re looking for a security framework that can provide continuous monitoring, strong access control policies, and improved device security, then BeyondCorp is undoubtedly worth considering.
Conclusion
In conclusion, network security is a critical concern for businesses in today’s digital landscape. Traditional network security models have limitations that can leave businesses vulnerable to cyber threats. BeyondCorp provides a solution that prioritizes user identity and device security. It enables businesses to better manage access control policies and monitor network activity.
The Zero Trust security model used by BeyondCorp offers continuous protection against potential cyber threats. It is regardless of where employees and contractors access the network. By implementing BeyondCorp, businesses can establish a more secure and scalable network infrastructure. That can adapt to the changing threat landscape.
Google’s implementation of it provides a real-world example of the framework’s effectiveness Google reports significant improvements in security and productivity. However, businesses need to evaluate their unique needs and challenges when considering it to adopt BeyondCorp.
BeyondCorp offers a cutting-edge security framework that helps businesses overcome the limitations of traditional network security models. And it provides better protection against cyber threats. It prioritizes user identity and device security over network location. This security model enables businesses to establish a more secure and adaptive network infrastructure. That will keep up with the evolving threat landscape.







