Introduction to Rainbow Table Attack
In digital technology, passwords serve as the first line of defense against any unauthorized access. However, hackers and cybercriminals constantly develop advanced techniques to crack passwords and compromise sensitive data. One such method is the Rainbow Table Attack. The Rainbow table attack is a powerful password-cracking technique. It exploits precomputed hash tables to break encrypted passwords rapidly.
Unlike brute-force attacks that try every possible password combination from scratch. Rainbow tables significantly speed up the process by using precomputed hashes. This makes them a serious threat to systems using weak or unsalted hashing algorithms.
In this blog post, let us explore how rainbow table attacks work, and why they are dangerous. And we explain most importantly, how to protect yourself against them. Let’s dive in!
What is a Rainbow Table?
A rainbow table is a precomputed database of hash values used to reverse cryptographic hash functions. That is primarily for cracking passwords. Instead of brute-forcing every possible password in real-time, attackers use these pre-generated tables to quickly find the original password corresponding to a given hash.
How Does a Rainbow Table Work?
- Hashing Basics: When a user creates a password, it is converted into a fixed-length hash using a hashing algorithm like MD5, SHA-1, or SHA-256.
- Precomputed Hashes: A rainbow table stores millions of these hash-password pairs in advance. That covers a vast range of possible passwords.
- Hash Matching: When an attacker obtains a hashed password from a database breach, they simply look it up in the rainbow table to find the matching plaintext password.
Why Are Rainbow Tables Used?
- They speed up password cracking significantly compared to traditional brute-force attacks.
- They are effective against systems using unsalted or weak hashing algorithms.
- They allow attackers to crack multiple hashes at once without recalculating every time.
However, modern security practices like salting and stronger hashing methods have reduced the effectiveness of rainbow tables. That is making them less common today.
What is a Rainbow Table?
Definition and Purpose of Rainbow Table
A rainbow table is a precomputed table containing hash values of passwords. It is used to reverse cryptographic hash functions efficiently. The precomputed table makes it a powerful tool for password cracking. Instead of generating and testing hash values in real-time, rainbow tables allow attackers to perform a quick lookup to find the original password corresponding to a given hash.
The primary purpose of a rainbow table is to speed up the process of recovering plaintext passwords from their hash values. Usually, many systems store passwords in a hashed format for security. Cybercriminals use rainbow tables to bypass the need for traditional brute-force attacks. That reduces the time required to crack a password.
For example, if a website’s password database is breached, and the passwords are hashed using MD5, then an attacker can use a rainbow table with precomputed MD5 hashes to quickly determine the original passwords.
History & Evolution of Rainbow Tables
Early Days of Password Storage
In the early days of computing, passwords were stored as plain text in system files. This made them extremely vulnerable. Anyone with access to these files could directly read passwords. To improve security, hashing algorithms were introduced to store passwords in an encoded format instead of plain text.
The Rise of Hash-Based Password Storage
By the 1970s, operating systems like UNIX implemented hashed password storage. It uses functions like DES-based crypt(). Instead of storing passwords directly, the system stored their hashed versions. One-way transformations that made it difficult to retrieve the original password.
However, as computing power increased, hackers began exploiting weak hashing methods using brute-force and dictionary attacks. This led to the creation of precomputed hash tables. That significantly sped up password cracking.
The Introduction of Precomputed Hash Tables
The concept of precomputed hash tables emerged in the 1990s. Attackers began building large datasets of common passwords and their corresponding hashes. Instead of brute-forcing each password, they could simply look up the hash in a table to instantly recover the original password.
The problem with traditional precomputed hash tables was their enormous size. Storing hashes for every possible password requires huge amounts of storage. That is making them impractical for large-scale attacks.
The Birth of Rainbow Tables (2003)
In 2003, Philippe Oechslin introduced rainbow tables as an optimized alternative to traditional hash tables. His technique was called “faster time-memory trade-off”. It reduced storage requirements by using chain-based hashing. Instead of storing every hash, rainbow tables stored only selected intermediate values and used a reduction function to regenerate missing hashes when needed.
This innovation made password cracking significantly more efficient. That allows attackers to break hashed passwords much faster than brute-force attacks while requiring far less storage space.
Security Response: Stronger Hashing Techniques
As rainbow table attacks became widespread, security researchers and developers began implementing stronger protections:
- Salting (Randomizing hashes) – Making each password hash unique. That is rendering rainbow tables useless.
- Key Stretching (Increasing hash computation time) – Using algorithms like PBKDF2, bcrypt, and Argon2, which slow down password hashing to resist precomputed attacks.
- Stronger Hashing Algorithms – Moving away from vulnerable hashes like MD5 and SHA-1 to more secure alternatives like SHA-256, bcrypt, and Argon2.
Modern-Day Password Security
Today, rainbow table attacks are far less effective against properly hashed and salted passwords. However, they still pose a threat when outdated or weak hashing algorithms are used.
With advancements in computing, including GPU-accelerated attacks and quantum computing, password security continues to evolve. Many organizations are now moving towards passwordless authentication (biometrics and hardware keys) to further reduce the risk of password-based attacks.
How Raibow Table Differs from Normal Hash Tables
At first glance, a rainbow table may seem similar to a traditional hash table. It stores a direct mapping of passwords and their respective hashes. However, rainbow tables use an advanced technique called chain reduction to make them much more space-efficient.
Key Differences between Normal Hash Tables and Rainbow Tables
| Feature | Normal Hash Table | Rainbow Table |
| Storage Requirement | Extremely large (stores each password-hash pair individually) | Significantly smaller due to chaining |
| Speed | Very fast (direct lookup) | Slightly slower (requires chain traversal) |
| Efficiency | Requires massive storage space | Balances storage and speed efficiently |
| Scalability | Not scalable due to size | More scalable for large datasets |
Understanding the Chain Reduction Technique
- Hash tables store every possible password and its hash that requires enormous storage space.
- Rainbow tables reduce storage by grouping hashes into chains. In which, each chain consists of multiple hashes linked together through a reduction function.
- Instead of storing every password-hash pair, a rainbow table only stores the first and last hash in a chain. Besides, it uses a predefined algorithm to regenerate intermediate values when needed.
This method significantly reduces storage requirements while maintaining efficiency in finding password matches.
Why Hackers Use Rainbow Tables for Password Cracking
Hackers prefer rainbow tables because they offer a faster and more efficient alternative to brute-force and dictionary attacks. Here is why they are so effective:
- Fast Password Recovery
Instead of computing millions of possible passwords and their corresponding hashes, attackers can simply look up the hash in the rainbow table and retrieve the original password within seconds. This saves computational power and time compared to brute-force attacks.
- Optimized Storage Usage
While traditional hash tables require huge amounts of storage (sometimes terabytes or more), rainbow tables compress data using chain-reduction techniques. That makes them more practical for large-scale password cracking.
- Effective against Unsalted Hashes
Many older systems and weakly secured databases store passwords without salting (adding a random value to each password before hashing).
- If a system does not use salting, rainbow tables can crack multiple password hashes at once, making them extremely powerful.
- For example, if thousands of users have the same password (password123), a rainbow table can reveal it immediately. In addition, it is exposing multiple accounts at once.
Limitations of Rainbow Tables
Despite their efficiency, rainbow tables have some drawbacks:
- Ineffective Against Salting – Modern security practices use salting. That is appends a unique random string to each password before hashing. This prevents rainbow tables from being used effectively because each hash is unique, even for identical passwords.
- Limited to Precomputed Hashes – A rainbow table is only effective for hashes that have already been precomputed. If an attacker encounters a password hash that is not in the table then they will need to compute new hashes, negating the speed advantage.
- Large Precomputed Tables Needed – Although rainbow tables reduce storage compared to normal hash tables. They still require huge precomputed datasets for longer and more complex passwords.
A rainbow table is a powerful password-cracking technique. It allows hackers to reverse cryptographic hashes efficiently using precomputed tables. Brute-force attacks generate every possible password combination on the fly. However, rainbow tables offer faster password recovery by leveraging stored hash chains.
However, modern security measures akin to salting, stronger hashing algorithms, and multi-factor authentication have made rainbow table attacks less effective. Still, they remain a significant cybersecurity threat for systems using weak password protection methods.
What is a Rainbow Table Attack?
Definition and Concept
A rainbow table attack is a password-cracking technique. It leverages precomputed tables of hash values to reverse cryptographic hashes quickly. This method is used to recover plaintext passwords from their hashed representations without performing real-time brute-force calculations.
Instead of hashing and testing potential passwords one at a time (as in brute-force attacks), rainbow tables store vast collections of hash-password pairs. That allows attackers to find the original password for a given hash almost instantly.
These attacks are especially effective when systems use weak hashing algorithms (MD5, SHA-1) and do not employ salting. Salting is a technique that adds random data to passwords before hashing to prevent precomputed attacks.
How It Works in Cracking Hashed Passwords
When a user creates a password, most secure systems do not store the actual password. Instead, they store a hashed version of it. Hashing is a one-way function that converts the password into a fixed-length string.
For example, using MD5:
- Password: 123456
- MD5 Hash: e10adc3949ba59abbe56e057f20f883e
The system only stores e10adc3949ba59abbe56e057f20f883e. That makes it impossible to retrieve the original password just by looking at the stored data.
However, an attacker with a rainbow table containing precomputed MD5 hashes can easily look up the hash and retrieve the original password. This completely bypasses the need for brute-force guessing.
Step-by-Step Breakdown of a Rainbow Table Attack
- Attacker Obtains a Hashed Password Database
- This can happen through data breaches, malware infections, or insider threats.
- The database contains usernames and their hashed passwords. However, it does not contain the plaintext versions.
- Checking for Matching Hashes in a Rainbow Table
- Instead of computing hashes for every possible password, the attacker uses a precomputed rainbow table that already contains millions (or even billions) of hash-password pairs.
- The attacker searches for the target hash within this table.
- Retrieving the Original Password
- If the hash is found in the table then the attacker can instantly recover the plaintext password associated with it.
- If the password is commonly used (password123) then it is highly likely to be present in a rainbow table.
- Exploiting the Cracked Password
- The attacker logs into the victim’s account using the recovered password.
- If the victim reuses passwords across multiple platforms then the attacker can access emails, social media, banking accounts, or corporate networks with the same credentials.
Example Scenario: A Real-World Rainbow Table Attack
Scenario: A Website Using MD5 Hashed Passwords without Salting
Step 1: Data Breach Exposes a Hashed Password Database
An attacker hacks into a website’s database and steals a list of hashed passwords. The database entries look something like this:
| Username | Hashed Password (MD5) |
| alice | 5f4dcc3b5aa765d61d8327deb882cf99 |
| bob | e10adc3949ba59abbe56e057f20f883e |
| charlie | 5ebe2294ecd0e0f08eab7690d2a6ee69 |
These are not plaintext passwords, so the attacker cannot use them directly.
Step 2: Using a Rainbow Table
The attacker has a rainbow table containing millions of precomputed MD5 hash-password pairs. They search the stolen hashes in their table and find matches:
| Hashed Password (MD5) | Recovered Password |
| 5f4dcc3b5aa765d61d8327deb882cf99 | password |
| e10adc3949ba59abbe56e057f20f883e | 123456 |
| 5ebe2294ecd0e0f08eab7690d2a6ee69 | secret |
Step 3: Exploiting the Cracked Passwords
Now, the attacker knows that:
- Alice’s password is “password”
- Bob’s password is “123456”
- Charlie’s password is “secret”
They can now:
Log into the accounts of Alice, Bob, and Charlie.
Try the same passwords on other websites (since many users reuse passwords).
Sell the credentials on the dark web for financial gain.
Why Rainbow Table Attacks Are Effective
- Faster Than Brute-Force Attacks
- Brute-force attacks generate and test passwords one by one. That is slow.
- Rainbow tables use precomputed hashes. That allows attackers to instantly find passwords instead of calculating them on the fly.
- Optimized Storage Using Chain Reduction
- Instead of storing every possible password-hash pair, rainbow tables use chains to reduce storage requirements while maintaining efficiency.
- Effective Against Systems Without Salting
- If a system hashes passwords without adding a unique salt value then every user with the same password will have the same hash.
- Rainbow tables exploit this weakness to crack multiple passwords at once.
Limitations of Rainbow Table Attacks
Despite their effectiveness, rainbow table attacks have several limitations:
- Ineffective Against Salted Hashes
- Modern security practices use salting. Salting adds a random value to each password before hashing.
- Example:
- Password: password123
- Salt: random123
- Hashed Output: a2f55c14de5b3a…
- Even if multiple users have the same password then salting ensures they have different hashes. That makes rainbow tables useless.
- Large Storage Requirements for Stronger Hashes
- Rainbow tables require huge precomputed datasets.
- As password lengths and complexity increase, the size of rainbow tables grows exponentially.
- Not Useful for Modern Hashing Algorithms
- Older hash functions like MD5 and SHA-1 are vulnerable to rainbow table attacks.
- Modern hashing algorithms like bcrypt, PBKDF2, and Argon2 are resistant because they are designed to be computationally expensive. That is making precomputed tables impractical.
A rainbow table attack is a powerful method used by hackers to reverse password hashes quickly using precomputed tables. It is significantly faster than brute-force attacks. It can compromise multiple accounts at once if passwords are stored without salting.
However, modern security measures—such as salting, strong hash functions, and multi-factor authentication (MFA). That has made rainbow table attacks less effective against well-secured systems.
How Do Rainbow Tables Work?
Rainbow tables are a powerful precomputed password-cracking technique. It is used by hackers to efficiently reverse cryptographic hashes into plaintext passwords. Brute-force attacks try every possible combination in real-time. However, rainbow tables use precomputed hash chains to match and retrieve passwords much faster.
Let us explore how rainbow tables work in detail.
- Understanding Hash Functions and Precomputed Tables
What is a Hash Function?
A hash function is a one-way cryptographic algorithm that transforms input data (such as a password) into a fixed-length, unique output known as a hash value. Hash functions are commonly used in security systems to store passwords safely.
For example, using the MD5 hashing algorithm:
- Password: letmein
- MD5 Hash: 0d107d09f5bbe40cade3de5c71e9e9b7
If a hacker gains access to this hash then they will not immediately know the original password unless they can reverse the hash. That is where rainbow tables come into play.
Why are Hash Functions Considered Secure?
- One-Way Function – Hash functions are designed to be irreversible.
- Deterministic – The same input always produces the same hash.
- Unique Output – Small changes in input drastically change the hash (Avalanche Effect).
- Fast Computation – Easy to generate. However, it is difficult to reverse.
However, hackers exploit weak hash functions (MD5, SHA-1) by using rainbow tables to precompute and store millions of hash-password pairs. Fast computation enables them instant lookups to crack passwords.
- The Process of Storing and Matching Hashes
A rainbow table is a large precomputed database of hash-password pairs. That helps attackers quickly find the original password associated with a given hash.
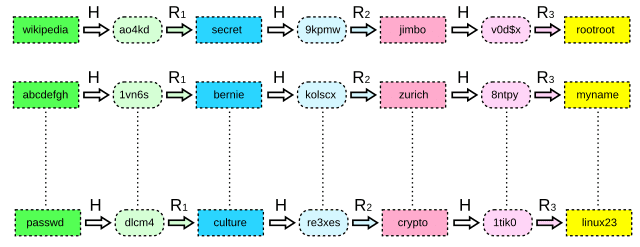
Step 1: Creating a Chain of Hashes
Instead of storing every possible password-hash pair (which would be too large), rainbow tables use a technique called chain reduction to efficiently compress and organize the data.
Process of Creating a Chain:
- Start with a plaintext password – Example: apple123.
- Hash it using a weak algorithm like MD5.
- Apply a reduction function to transform the hash into a new password guess.
- Hash the new password and repeat the process.
- Store only the first and last values in the chain. That is significantly reducing storage space.
Example Chain Using MD5 Hashing & Reduction Process:
| Step | Password | MD5 Hash | Reduced Password |
| 1 | apple123 | eb31eeb0… | grape99 |
| 2 | grape99 | 7c4a8d09… | banana22 |
| 3 | banana22 | dc647eb6… | cherry77 |
| 4 | cherry77 | 0cc175b9… | watermelon88 |
Only apple123 (starting password) and watermelon88 (final password in the chain) are stored in the rainbow table.
Step 2: Cracking a Hash Using a Rainbow Table
When an attacker finds a stolen hashed password (from a data breach), they:
- Search for the hash in the rainbow table.
- If the hash is not directly found then they recreate the hash chain using reduction functions.
- Once they reach a known value in the table then they backtrack to recover the original password.
Example Lookup Process:
- Target hash: dc647eb6…
- Found in a chain with endpoint watermelon88.
- Reversing the chain reveals the original password: banana22.
This lookup process is much faster than brute-force attacks, as it does not require hashing every possible password during the attack.
-
Efficiency of Rainbow Tables vs. Brute-Force Attacks
Comparison of Password Cracking Techniques
| Attack Method | How It Works | Speed | Storage Needed | Effectiveness |
| Brute-Force Attack | Hashes and tests every possible password one by one. | Very slow | Minimal | Low for long passwords |
| Dictionary Attack | Uses a list of common passwords and their hashes. | Faster than brute-force | Medium | Moderate |
| Rainbow Table Attack | Uses precomputed hashes to find passwords instantly. | Very fast | Very large | High (if no salting is used) |
Why Are Rainbow Tables Faster?
- No need to hash each password during an attack – Since the hashes are precomputed, attackers just perform quick lookups.
- Lookup is near-instantaneous for weak hash functions like MD5 and SHA-1.
- Multiple passwords can be cracked at once if they share the same hash function.
-
Limitations of Rainbow Table Attacks
Rainbow tables are powerful. However, they have certain limitations:
- Ineffective Against Salting
Modern password storage techniques use salting. Salting appends a random string to each password before hashing it. This ensures that even identical passwords generate different hashes. That makes rainbow tables useless.
Example:
- Password: letmein
- Salt: X7a9@!b3
- Hashed Output (SHA-256): e1faffb3e614e6c2fba74296962386b7
Since each password has a unique salt, a single rainbow table cannot be used to crack all passwords.
- Large Storage Requirement
Even though rainbow tables use chain reduction, they still require massive storage space. For example, a full MD5 rainbow table for 8-character passwords can be hundreds of terabytes in size.
- Ineffective Against Slow Hashing Algorithms
Rainbow tables are designed for fast hash functions (MD5, SHA-1). However, modern algorithms like bcrypt, PBKDF2, and Argon2 introduce computational delays that make rainbow tables impractical.
Key Takeaways
Rainbow tables use precomputed hash chains to crack passwords faster than brute-force attacks.
they work well against weak hash functions. However, they fail against salted passwords.
Brute-force attacks are slower. However, they do not require large storage space.
Using strong, slow hashing algorithms like bcrypt or Argon2 makes rainbow tables ineffective.
Why Are Rainbow Table Attacks Dangerous?
Rainbow table attacks are one of the most efficient password-cracking techniques. It has the ability to quickly retrieve plaintext passwords from hashed values. Compared to brute-force or dictionary attacks, rainbow tables allow attackers to break passwords at an accelerated speed. That makes them a serious cybersecurity threat.
This section explores why rainbow table attacks are dangerous, how they impact online security, and real-world incidents where they have been exploited.
-
The Speed and Effectiveness of Rainbow Table Attacks
One of the biggest reasons rainbow table attacks are dangerous is their speed. In brute-force attacks, an attacker has to generate a new hash for every guessed password. However, a rainbow table attack uses precomputed hashes to crack passwords almost instantly.
How Does It Compare to Other Attacks?
| Attack Type | How It Works | Speed | Effectiveness | Storage Required |
| Brute-Force Attack | Tries all possible passwords until the correct one is found. | Slow (especially for long passwords) | Moderate to High | Low |
| Dictionary Attack | Uses a list of common passwords to check against the hash. | Faster than brute-force | Moderate | Medium |
| Rainbow Table Attack | Matches precomputed hash chains to hashed passwords. | Very Fast | High (if hashing is weak) | High (requires large tables) |
Why Are Rainbow Tables So Fast?
- Since the hashes are already computed, the attack only needs to match the stored hash to a precomputed hash.
- Attackers can reuse the same rainbow table for any database that uses the same hashing algorithm.
- Computational power is minimized. That is making the attack much more efficient than brute-force attempts.
Real-world impact: If a hacker obtains a leaked database of hashed passwords (from a data breach) then they can use a rainbow table to crack thousands of passwords within minutes.
-
Impact on Weakly Hashed or Unsalted Passwords
Rainbow table attacks exploit weak hashing methods. Many websites still use outdated algorithms that are vulnerable to precomputed tables. Using weak hashing makes it easier for attackers to retrieve passwords.
Which Hashing Methods Are Vulnerable?
MD5 (Message Digest Algorithm 5) – It is one of the most widely used but easily broken hashing methods. Most MD5 hashes are precomputed and stored in rainbow tables.
SHA-1 (Secure Hash Algorithm 1) – Although more secure than MD5, it is still susceptible to rainbow table attacks, when used without Salting.
Unsalted SHA-256 or SHA-512 – Even stronger hashing algorithms like SHA-256 and SHA-512 are vulnerable if they are not salted.
What Happens If a Password Is Unsalted?
Without a salt, a password always produces the same hash. This means:
- Attackers can crack multiple users’ passwords at once if they use common passwords.
- A precomputed rainbow table can be reused indefinitely. That is making attacks extremely efficient.
- Once one password is cracked, it can be used to access other accounts if users reuse passwords across platforms.
Example:
Let us say the password is “welcome123”.
- If an unsalted MD5 hash is used then it always results in:
- 5e9f9e8f7a7f5b7e6d8f7c6b6a5e4d3c
- This hash is already stored in rainbow tables, so an attacker can instantly recover the password.
-
Real-World Cyberattack Examples
Several high-profile data breaches have been exploited using rainbow table attacks due to weak hashing methods. Here are some examples:
LinkedIn Data Breach (2012, 2016)
- What happened?
- In 2012, 6.5 million hashed LinkedIn passwords were leaked.
- In 2016, an additional 117 million user credentials were exposed.
- The passwords were hashed using unsalted SHA-1. That made them easy to crack with rainbow tables.
- Result:
- Millions of passwords were decrypted within a few hours.
- Many users had reused passwords across different sites. That was leading to further attacks.
Adobe Data Breach (2013)
- What happened?
- A massive data breach exposed 153 million Adobe user credentials.
- Adobe used poor encryption techniques without proper salting. That allowed attackers to decrypt most passwords quickly.
- Result:
- Hackers used rainbow tables to break thousands of passwords within a short period.
- Many users had used weak passwords like “123456”, “password”, and “adobe123”. That was making them easy targets.
RockYou Data Breach (2009)
- What happened?
- Over 32 million plaintext passwords were stolen from RockYou.
- These passwords were stored without any encryption or hashing.
- Result:
- The RockYou password list became a major source for rainbow tables and brute-force attacks.
- Today, hackers still use the RockYou wordlist to generate rainbow tables for attacks.
-
Why Do Cybercriminals Prefer Rainbow Table Attacks?
Hackers and cybercriminals prefer rainbow table attacks because they:
Require minimal computing power – Instead of generating hashes in real time then attackers only need to compare values.
Can break multiple passwords at once – If an attacker has a leaked password database then all weakly hashed passwords can be cracked simultaneously.
Bypass traditional security measures – If an organization does not use salting then rainbow table attacks can easily defeat basic encryption techniques.
Work on old and poorly secured systems – Many legacy systems still use MD5 or SHA-1 without salt. That makes them ideal targets.
-
How to Protect Against Rainbow Table Attacks
To prevent rainbow table attacks, organizations and individuals should adopt strong security measures:
Use Strong, Slow Hashing Algorithms
- Instead of using MD5 or SHA-1, opt for bcrypt, PBKDF2, or Argon2.
- These algorithms introduce computational delays. The computational delays make rainbow tables impractical.
Always Implement Salting
- Salting adds a random value to each password before hashing. That makes precomputed attacks ineffective.
- A strong salt should be unique for each user.
Enforce Strong Password Policies
- Encourage users to create long, complex passwords.
- Avoid using common passwords that can be found in rainbow tables.
Enable Multi-Factor Authentication (MFA)
- Even if a password is cracked then MFA prevents unauthorized logins.
Regularly Update Security Practices
- If your system still uses MD5 or SHA-1 then migrate to a modern hashing algorithm immediately.
- Conduct regular security audits to detect vulnerabilities.
Rainbow table attacks are one of the most efficient and dangerous password-cracking techniques. When weak hashing methods are used, attackers can crack millions of passwords in minutes using precomputed tables.
The best way to protect against these attacks is to use salting, implement strong hashing algorithms, and enforce robust security measures.
Defenses against Rainbow Table Attacks
A rainbow table attack is a serious cybersecurity threat. It happens particularly to systems that store passwords with weak or unsalted hash functions. Cybercriminals use precomputed hash tables to quickly match password hashes to their plaintext counterparts. The precomputed hash tables allow them to bypass authentication systems effortlessly.
To prevent these attacks, organizations and individuals must adopt modern security practices to fortify password protection. Below are the most effective defenses against rainbow table attacks.
-
Use Strong and Modern Hashing Algorithms
Why Weak Hashing Algorithms Are Vulnerable
Older hashing algorithms like MD5, SHA-1, and unsalted SHA-256 are highly vulnerable to rainbow table attacks because they:
- Generate deterministic hash values (the same input always produces the same output).
- They are computationally fast that is making it easier to precompute rainbow tables.
- The lack of built-in salting allows attackers to use the same precomputed tables for multiple accounts.
Recommended Hashing Algorithms
To counter rainbow table attacks, it is crucial to use modern, slow, and computationally expensive hashing functions, such as:
bcrypt – It includes a built-in salting mechanism and allows for work factor adjustments to slow down brute-force attacks.
PBKDF2 (Password-Based Key Derivation Function 2) – It uses multiple iterations to make brute-force and precomputed attacks infeasible.
Argon2 – It is the winner of the Password Hashing Competition (PHC). It is designed to be memory-intensive and resistant to brute-force attempts.
How Secure Hashing Prevents Rainbow Table Attacks
Slower Computation – A slow hashing function makes precomputing and storing massive rainbow tables impractical.
Dynamic Security – Some hashing algorithms like bcrypt allow increasing computational difficulty over time to match hardware advancements.
Unique Hash Outputs – Functions like Argon2 and PBKDF2 introduce randomness. That is making precomputed hash attacks ineffective.
- Implement Salting to Hashes
What is Salting?
A salt is a random, unique value added to each password before hashing. It ensures that even if two users have the same password then their stored hashes will be different.
Example without Salt
- Password: password123
- Hash: ef92b778bafe771e89245b89ecbc583c (MD5)
Example with Salt
- Salt: x8z4j@9k
- Password + Salt: password123x8z4j@9k
- Hash: adf74f57e6a2c0c2d06f7b902b12e5df
Why Salting Is Effective
Prevents Precomputed Attacks – Attackers cannot reuse existing rainbow tables.
Ensures Unique Hashes – Two identical passwords will have completely different hashes.
Defends Against Mass Credential Exposure – If a hacker steals one password hash even they cannot apply the same attack to other users.
Bad Security Practice: Using the same salt for every user defeats the purpose of salting. Always generate a unique salt for each password.
-
Use Peppering for Additional Security
A pepper is another random value added to a password before hashing. However, unlike a salt, it is not stored in the database. Instead, it is stored in the application code or a separate secure system.
| Method | Stored in a Database? | Purpose |
| Salting | Yes | Prevents identical hashes for identical passwords. |
| Peppering | No | Adds an additional layer of security. That is making attacks harder. |
How Peppering Strengthens Security
Even if an attacker gains access to hashed passwords; they still need the secret pepper to crack them.
Prevents dictionary and brute-force attacks, even if salting is compromised.
Makes hash cracking significantly harder. The attackers cannot derive rainbow tables for peppered hashes.
Example Implementation:
- Password: password123
- Salt: xyz123@!
- Pepper (Stored separately): SuperSecretKey
- Hashed Value: HASH (password123 + xyz123@! + SuperSecretKey)
-
Implement Rate-Limiting and Account Lockout Policies
Even with strong password hashing, attackers may attempt brute-force attacks by repeatedly trying different passwords. Rate-limiting restricts how many attempts a user can make in a certain period.
Best Practices for Login Security
Account Lockout Mechanisms – Lock the account after 5-10 failed login attempts for a set period.
Progressive Time Delay – Increase delay after each failed attempt (5 seconds, then 30 seconds, then 1 minute).
CAPTCHA Implementation – Prevents bots from launching automated attacks.
Example: If a hacker tries 1000 password attempts per second then rate-limiting reduces this to just a few attempts per minute. That is making brute-force infeasible.
-
Enforce Multi-Factor Authentication (MFA)
Even if an attacker cracks a password, Multi-Factor Authentication (MFA) ensures they cannot access the account without additional verification.
Common MFA Methods
One-Time Passwords (OTP) – Sent via SMS, email, or authentication apps.
Biometric Authentication – Fingerprint, facial recognition, retina scans.
Hardware Security Keys – YubiKey, Google Titan Security Key.
Example: Even if an attacker successfully cracks a password then they still need the user’s phone or biometric authentication to log in.
-
Encrypt Passwords Instead of Plaintext Hashing
Instead of storing password hashes directly, encrypting password databases using AES (Advanced Encryption Standard) adds another layer of security.
| Method | Reversible? | Best For? |
| Hashing | No | Storing passwords securely. |
| Encryption | Yes (With decryption key) | Protecting sensitive data (credit card details). |
Best Practices for Password Encryption
Store encryption keys in separate, secure locations.
Use Hardware Security Modules (HSM) to manage encryption.
Rotate encryption keys periodically to mitigate leaks.
-
Regularly Update Security Policies
Cyber threats evolve rapidly. Organizations should:
Migrate from weaker algorithms (MD5, SHA-1) to bcrypt, PBKDF2, or Argon2.
Force password resets periodically to eliminate outdated vulnerabilities.
Monitor for leaked credentials using services like “Have I Been Pawned?”
Rainbow table attacks are a serious cybersecurity threat. However, they can be mitigated with modern security practices.
Key Takeaways:
Use bcrypt, PBKDF2, or Argon2 instead of MD5/SHA-1.
Always apply salting and peppering to password hashes.
Implement rate-limiting, account lockouts, and CAPTCHA to prevent automated attacks.
Enable MFA to add an extra layer of security.
Regularly update hashing algorithms and monitor security breaches.
Follow these best practices to effectively prevent rainbow table attacks and safeguard user credentials.
Rainbow Table vs. Brute Force vs. Dictionary Attacks
Cybercriminals use different techniques to crack passwords. Their techniques depend on the strength of the encryption and the security measures in place. Among the most common methods are Rainbow Table Attacks, Brute Force Attacks, and Dictionary Attacks. Each approach has its strengths and weaknesses. However, understanding their differences is essential for implementing effective cybersecurity defenses.
-
Brute Force Attack
Definition
A brute force attack is a trial-and-error method where an attacker tries every possible combination of characters until the correct password is found. This is the most straightforward but computationally expensive way of cracking passwords.
How It Works
- The attacker sets up an automated script or tool that generates all possible passwords within a given length and character set.
- Each generated password is hashed and then compared with the stored password hash in the system.
- If a match is found then the original password is successfully cracked.
Advantages of Brute Force Attacks
Guaranteed to work eventually – If given enough time and resources then brute force can crack any password.
Does not rely on precomputed data – It works in real-time. It works without needing stored password lists.
No dependency on password structure – It does not rely on common words or patterns. That makes it more universal.
Disadvantages of Brute Force Attacks
Extremely slow for long and complex passwords – If more characters are in the password then it takes a longer time to attack.
High computational cost – Brute-force attacks require significant processing power and memory.
Easily mitigated with strong passwords – Using longer and more complex passwords makes brute-force attacks impractical.
Example of a Brute Force Attack
Let us assume a password is 4 characters long and consists of lowercase letters (a-z). A brute force attack would attempt:
- aaaa
- aaab
- aaac
- …
- zzzz
The number of possible combinations = 26^4 = 456,976.
Now, if the password is 8 characters long then the total number of possibilities increases to 26^8 = 208,827,064,576. This exponential growth makes brute force impractical for long passwords.
-
Dictionary Attack
Definition
A dictionary attack is an optimized version of brute force that does not try every possible combination. Instead, it uses a predefined list of commonly used passwords to attempt access.
How It Works:
- The attacker gathers a wordlist containing the most commonly used passwords (password123, qwerty, admin, iloveyou).
- Each password in the wordlist is hashed and compared against the stored password hash.
- If a match is found then the attacker successfully retrieves the original password.
Advantages of Dictionary Attacks
Faster than brute force – It only tests commonly used passwords rather than every possible combination.
Low computational cost – Since only a small subset of passwords is tested, it requires less processing power.
Effective against weak passwords – Many users still use predictable passwords. That makes dictionary attacks highly effective.
Disadvantages of Dictionary Attacks
Limited to the passwords in the wordlist – It cannot crack passwords that are not in the dictionary.
Fails against strong, complex passwords – Randomized or highly unique passwords are immune.
Can be prevented by enforcing strong password policies – Requiring complex passwords renders dictionary attacks ineffective.
Example of a Dictionary Attack
A hacker might use a wordlist containing the following common passwords:
- 123456
- password
- letmein
- football
- monkey
- welcome123
If a user’s password matches one of these entries then the hacker can crack it in seconds.
-
Rainbow Table Attack
Definition
A rainbow table attack is an advanced password-cracking technique that uses precomputed hash values to reverse-engineer stored password hashes quickly. Instead of generating and comparing hashes in real time (like brute force), it relies on massive lookup tables to find matches instantly.
How It Works
- The attacker precomputes hashes for a vast number of possible passwords and stores them in a rainbow table.
- When they obtain a hashed password from a data breach, they search for its match in the rainbow table.
- If a matching hash is found then the corresponding plaintext password is retrieved immediately.
Advantages of Rainbow Table Attacks
Much faster than brute force and dictionary attacks – Precomputed hashes allow for instant password retrieval.
Less computationally intensive – The hashing process is done beforehand. That is reducing real-time processing.
Highly effective against unsalted hashes – If a system does not use salting then rainbow tables can crack thousands of passwords in seconds.
Disadvantages of Rainbow Table Attacks
Requires massive storage space – Storing precomputed hashes for a wide range of passwords takes up terabytes of disk space.
Defeated by salting – If each password hash is stored with a unique salt then rainbow tables become ineffective.
Limited to the range of precomputed hashes – If a password is not within the rainbow table’s dataset then the attack fails.
Example of a Rainbow Table Attack
Let us say a user’s password is password123, and the system stores it as a hash:
ef92b778bafee2efcbeff45d02c48710
If a hacker has precomputed the hash for password123 in their rainbow table then they can instantly find a match and retrieve the plaintext password.
Comparison of Hashing Algorithms
| Algorithm | Hash Length | Speed | Salting? | Key Stretching? | Security Level | Vulnerability to Rainbow Tables | Use Cases |
| MD5 (Message-Digest Algorithm 5) | 128-bit | Very Fast | No | No | Weak – Broken | Highly Vulnerable (Precomputed rainbow tables exist) | Legacy systems (not recommended), checksum validation |
| SHA-1 (Secure Hash Algorithm 1) | 160-bit | Fast | No | No | Weak – Collision attacks exist | Highly Vulnerable (Easily cracked with rainbow tables) | Old certificates, legacy software (deprecated) |
| SHA-256 (Secure Hash Algorithm 256-bit) | 256-bit | Moderate | No | No | Stronger than MD5/SHA-1 but not ideal for passwords | Vulnerable if unsalted | Blockchain, data integrity verification, cryptographic applications |
| bcrypt | Variable (default: 184-bit) | Slow (adjustable cost factor) | Yes (Automatic) | Yes (Built-in key stretching) | Very Secure | Resistant (due to salting and slow hashing) | Password hashing, authentication systems |
| PBKDF2 (Password-Based Key Derivation Function 2) | Variable | Slow (Configurable iterations) | Yes | Yes | Secure if a high iteration count is used | Resistant (If high iteration count and salting are used) | Secure password hashing, encryption key derivation |
| Argon2 (Winner of Password Hashing Competition) | Variable | Slow (Memory-intensive, configurable) | Yes | Yes (Memory-hard function) | Most Secure | Highly Resistant (Designed to prevent attacks like rainbow tables) | Modern password hashing, authentication systems |
Key Takeaways:
- MD5 & SHA-1 are outdated. They are highly vulnerable to rainbow table attacks—avoid using them for password storage.
- SHA-256 is stronger. However, they are not ideal for password hashing because they lack salting and key stretching by default.
- bcrypt, PBKDF2, and Argon2 are the best choices for password security due to salting, key stretching, and slow computation.
- Argon2 is the most secure hashing algorithm today. It is memory-hard and designed to resist all forms of cracking, including rainbow tables.
-
Key Differences: Rainbow Table vs. Brute Force vs. Dictionary Attack
| Factor | Brute Force Attack | Dictionary Attack | Rainbow Table Attack |
| Speed | Slowest | Faster than brute force | Fastest |
| Storage Requirement | None | Small | Very Large |
| Effectiveness | Works on all passwords | Works on common passwords | Works on unsalted passwords |
| Computational Cost | High | Moderate | Low (pre-computed) |
| Defense Mechanisms | Strong passwords, MFA | Unique and complex passwords | Salting, strong hashing algorithms |
Which is the Most Effective Attack Method?
- For Weak Passwords → Dictionary Attack is the fastest.
- For Any Password (given enough time) → Brute Force is guaranteed to work.
- For Precomputed Hash Cracking → Rainbow Table Attack is the fastest. However, it requires unsalted hashes.
- How to Defend Against All Three Attacks?
Use Strong Passwords – At least 12+ characters with uppercase, lowercase, numbers, and symbols.
Enable Multi-Factor Authentication (MFA) – Even if a password is cracked, MFA blocks unauthorized access.
Use Slow Hashing Algorithms – bcrypt, PBKDF2, Argon2 make brute-force attacks impractical.
Implement Salting – Prevents rainbow table attacks by making each hash unique.
Use Account Lockout & Rate-Limiting – Prevents automated attack attempts.
Each password-cracking method has its pros and cons. Brute force is the slowest. However, it works on all passwords. Dictionary attacks are faster. However, they are limited. Rainbow tables are extremely efficient but require unsalted hashes. The best defense is a combination of strong password policies, advanced encryption methods, and multi-layered authentication to prevent unauthorized access.
Role of Salting, Peppering, and Key Stretching in Preventing Attacks
To enhance password security and prevent attacks like rainbow table attacks, brute-force attacks, and dictionary attacks, security experts use three critical techniques. They are namely Salting, Peppering, and Key Stretching. Each of these techniques adds an extra layer of protection. That is making it significantly harder for attackers to crack passwords.
-
Salting – Adding Uniqueness to Hashes
What is Salting?
Salting involves adding a random, unique value (called a salt) to each password before hashing. The primary goal of salting is to ensure that even if two users have the same password; their stored hashes will be different.
How It Works:
- A user enters their password, e.g., password123.
- A unique, randomly generated salt (X7a$9P!l) is added to the password.
- The password + salt combination (password123X7a$9P!l) is hashed using a cryptographic hash function (bcrypt, SHA-256).
- The final hash is stored along with the salt in the database.
Why Is Salting Important?
Prevents rainbow table attacks, as attackers cannot precompute hashes without knowing the salt.
Ensures users with the same password have different hash values. That is making attacks less efficient.
It forces attackers to hash each password individually. That is increasing computational effort.
Limitations of Salting:
Salting alone does not slow down attacks – attackers can still use brute-force methods to guess passwords.
Weak salts (fixed or predictable salts) can be ineffective if attackers know the salting pattern.
- Peppering – Adding a Secret Server-Side Key
What is Peppering?
Peppering is similar to salting. However, with a secret twist—instead of storing the pepper alongside the password, the pepper is kept secret on the server.
How It Works:
- A server-side secret value (pepper) is added to the password before hashing.
- Unlike salts, the pepper is not stored in the database—only the hash is saved.
- Attackers who steal the password database still need the secret pepper to brute-force hashes.
Why Is Peppering Important?
Adds an extra layer of security beyond salting. That is making it harder to crack stolen password hashes.
Prevents database leaks from being immediately exploitable—an attacker needs both the hashes and the secret pepper.
Useful for defending against offline attacks where an attacker has obtained hashed passwords.
Limitations of Peppering:
If the server is compromised then the pepper may be stolen. That is reducing its effectiveness.
Changing the pepper is complex—it requires rehashing all stored passwords.
- Key Stretching – Slowing Down Attackers
What is Key Stretching?
Key stretching is a technique that intentionally makes password hashing computationally expensive. The goal is to increase the time required for each brute-force attempt. That is discouraging attackers.
How It Works:
- Instead of hashing the password just once, key stretching applies the hash function multiple times (thousands or millions of iterations).
- The result is a longer processing time. That is making brute-force attacks slower and more costly.
- Common key stretching algorithms:
- PBKDF2 (Password-Based Key Derivation Function 2)
- bcrypt (Adjustable cost factor)
- Argon2 (Memory-hard function, winner of Password Hashing Competition)
Why Is Key Stretching Important?
Increases the time required for brute-force attempts. The increased time makes attacks computationally expensive.
Prevents rapid guessing of hashes, as each guess takes significantly longer.
Essential for securing weak passwords—even if users choose bad passwords, cracking takes much longer.
Limitations of Key Stretching:
Requires more processing power on the server. That may slow down authentication if misconfigured.
Older key stretching methods (like PBKDF2 with low iteration count) can still be cracked if not properly tuned.
How These Three Techniques Work Together
| Security Feature | Function | Benefit | Helps Prevent |
| Salting | Adds a unique random value to each password before hashing. | Ensures passwords with the same input do not have the same hash. | Rainbow table attacks |
| Peppering | Adds a secret server-side key to the password before hashing. | Even if the database is leaked, attackers cannot verify hashes easily. | Database breaches & offline attacks |
| Key Stretching | Increases the time needed to hash a password using multiple iterations. | Slows down brute-force attacks significantly. | Brute-force and dictionary attacks |
Salting, peppering, and key stretching should be used together for strong password security.
Modern hashing algorithms like bcrypt, Argon2, and PBKDF2 already implement these techniques effectively.
Weak passwords can still be exploited—users should use long, unique passwords alongside these defenses.
Popular Tools Used for Rainbow Table Attacks
Rainbow table attacks rely on pre-computed hash-to-password mappings. precomputed hash-to-password mappings allow attackers to crack passwords quickly compared to brute-force methods. Cybercriminals and penetration testers use specialized tools to execute these attacks. They often target unsalted password hashes. Below is a detailed look at some of the most widely used rainbow table attack tools. Let us discuss how they work, and how to defend against them.
-
Cain and Abel
Overview
Cain and Abel is one of the oldest and most powerful password recovery tools designed for Windows. Its primary use is to recover lost passwords. However, cybercriminals exploit it to steal and crack password hashes using various attack techniques, including rainbow tables.
Key Features
Supports rainbow table attacks for cracking Windows passwords.
Can intercept and analyze network traffic to extract password hashes.
Supports dictionary, brute-force, and cryptanalysis attacks.
Can recover stored passwords from local systems.
How Attackers Use It
- Attackers use Cain and Abel to capture password hashes from a compromised machine or network.
- They load rainbow tables into the tool. That allows them to quickly match the captured hashes to plaintext passwords.
- If the system uses outdated LM hashes (Windows XP and older) then the attack is almost instantaneous.
Defensive Measures
Use encrypted protocols (TLS/SSL) to prevent network sniffing.
Enable Windows security settings to disable LM hashing.
Implement strong, complex passwords to make precomputed attacks impractical.
-
Ophcrack
Overview
Ophcrack is one of the most widely used open-source password-cracking tools. It is known for its ability to crack Windows passwords using rainbow tables. It is available for Windows and Linux and even offers Live CD versions for offline password recovery.
Key Features
Uses precomputed rainbow tables to crack Windows LM and NTLM hashes.
Comes with free downloadable rainbow tables for common password sets.
Works on Windows XP, Vista, 7, 8, and some 10 versions.
Supports brute-force fallback if rainbow tables fail.
How Attackers Use It
- Attackers boot Ophcrack from a USB drive to access a target computer’s hashed password files.
- The software compares the hashes with rainbow tables to retrieve plaintext passwords.
- If the password is weak and unsalted then the attack takes seconds to minutes.
Defensive Measures
Disable LM hashing (Windows 10+ does this by default).
Use long and complex passwords to prevent easy matches.
Employ multi-factor authentication (MFA) to reduce reliance on passwords.
-
Rainbow Crack
Overview
Rainbow Crack is a command-line tool that uses precomputed rainbow tables to break password hashes. Unlike brute-force methods that generate hashes in real-time, Rainbow Crack significantly reduces cracking time by leveraging stored tables.
Key Features
Supports various hashing algorithms (MD5, SHA1, NTLM, etc.).
Allows users to generate custom rainbow tables.
Works on Windows and Linux.
Faster than traditional brute-force attacks.
How Attackers Use It
- Attackers obtain hashed passwords from databases or memory dumps.
- They run Rainbow Crack with a precomputed rainbow table for the hash type used.
- If a match is found then the password is cracked instantly.
Defensive Measures
Use salting techniques to make rainbow tables ineffective.
Adopt bcrypt, PBKDF2, or Argon2 for hashing instead of MD5 or SHA1.
Rotate passwords regularly to prevent long-term exposure.
-
Hashcat (with Rainbow Tables)
Hashcat is the fastest and most powerful password-cracking tool available today. It primarily supports brute-force and dictionary attacks. However, it can also leverage rainbow tables for certain cracking operations.
Key Features
Uses GPU acceleration, making it extremely fast.
Can crack MD5, SHA-256, NTLM, and many other hash types.
Works with rainbow tables, brute force, and hybrid attacks.
Compatible with Windows, Linux, and macOS.
How Attackers Use It
- Attackers load stolen password hashes into Hashcat.
- They apply rainbow tables for instant matches if a pre-computed hash exists.
- If no rainbow table match is found then they switch to brute-force attacks.
Defensive Measures
Use long, complex passwords to make brute force impractical.
Implement account lockout mechanisms to prevent repeated attacks.
Salting passwords makes rainbow tables ineffective.
-
L0phtCrack
Overview
L0phtCrack is a password auditing and recovery tool commonly used in corporate environments. It was originally created for penetration testing. However, hackers exploit it to crack weak password hashes.
Key Features
Supports Windows password cracking using rainbow tables.
Performs brute-force, dictionary, and hybrid attacks.
Includes password-strength auditing tools for enterprises.
Extracts and cracks password hashes from local Windows systems.
How Attackers Use It
- Attackers use L0phtCrack to assess weak passwords in enterprise networks.
- They load rainbow tables to crack unsalted password hashes.
- If a password is not found in the rainbow tables then they use brute force or hybrid attacks.
Defensive Measures
Enforce strong password policies across the organization.
Use two-factor authentication (2FA) for additional security.
Adopt slow hashing algorithms (Argon2, PBKDF2) to make cracking infeasible.
How Attackers Leverage These Tools: Step-by-Step Attack Process
- Stealing Password Hashes
- Attackers breach databases, intercept network traffic, or use malware to obtain password hashes.
- Tools like Mimikatz or network sniffers are used to extract credentials.
- Loading Hashes into Cracking Tools
- The attacker imports hashed passwords into tools like Ophcrack, Rainbow Crack, or Hashcat.
- Using Rainbow Tables for Instant Cracking
- Instead of generating hashes in real-time, the tool compares each hash to precomputed tables.
- If a match is found then the plaintext password is instantly recovered.
- Gaining Unauthorized Access
- With the cracked password, the attacker logs into systems, steals data, or escalates privileges.
- If the victim reuses passwords then attackers use them across multiple sites (credential stuffing).
Rainbow table attacks exploit weak password hashing by precomputing billions of possible hash values. Tools like Ophcrack, Rainbow Crack, and Hashcat enable attackers to recover passwords almost instantly. That makes it essential for organizations and individuals to adopt modern security measures such as:
Salting passwords to prevent precomputed hash attacks.
Using slow, memory-intensive hashing algorithms (Argon2, PBKDF2, bcrypt).
Enforcing strong password policies (long, complex, unique passwords).
Enabling multi-factor authentication (MFA) for additional protection.
How to Protect Yourself from Rainbow Table Attacks
Rainbow table attacks are one of the most efficient techniques used by cybercriminals to crack passwords. These attacks break weak or unsalted password hashes almost instantly. To safeguard user credentials and protect critical data, both individual users and organizations must implement strong security measures.
Best Security Practices for Users and Organizations
-
Use Salted Hashing Algorithms (Most Effective Defense)
A rainbow table attack is only effective when password hashes remain static (i.e., no additional randomness is introduced). This is where salting plays a critical role.
What is a Salt?
A salt is a random string of characters. That is added to a password before hashing. This makes each password hash unique, even if two users have the same password. Because of this, rainbow tables become ineffective, since attackers would need a separate rainbow table for every unique salt. That is practically impossible.
Recommended Hashing Algorithms with Salting:
bcrypt – Built-in salting and slow hashing process. It is ideal for password storage.
PBKDF2 – Uses multiple iterations to make password cracking harder.
Argon2 – A modern memory-intensive hashing algorithm designed to resist brute-force attacks.
Avoid Weak Hashing Algorithms:
MD5 and SHA-1 – Easily cracked using rainbow tables.
Unsalted SHA-256 – While stronger, it is still vulnerable without salting.
Key Takeaway: Always use a hashing algorithm that includes salting and key stretching to ensure strong security.
-
Implement Multi-Factor Authentication (MFA)
Even if an attacker cracks a password, MFA acts as a second line of defense by requiring additional authentication.
Effective MFA Options:
Authenticator apps (Google Authenticator, Microsoft Authenticator) – Generate temporary codes.
Hardware security keys (YubiKey, Titan Security Key) – Physical devices that add an extra layer of security.
Biometric authentication (Fingerprint, Face ID) – Reduces reliance on passwords.
Why MFA Works: Attackers must gain access to both the password and the second factor. That is making unauthorized access significantly harder.
-
Use Long, Complex Passwords
Even with salting and strong hash algorithms, short and weak passwords remain vulnerable. Longer passwords make it computationally expensive for attackers to crack them.
Strong Password Guidelines:
At least 12-16 characters long (longer is better).
Mix of uppercase, lowercase, numbers, and symbols.
Avoid common words, dictionary words, and predictable patterns ( “password123”).
Tip: Use a passphrase instead of a password. A phrase like “Purple$Sun@Rise2025” is both strong and easy to remember.
Avoid Reusing Passwords – If one password gets leaked then all accounts using the same password will be compromised.
-
Regularly Update and Rotate Passwords
Hackers often obtain password hashes from data breaches and use rainbow tables or brute-force attacks to crack them. Changing passwords regularly minimizes the risk.
How Often Should You Change Passwords?
Every 3-6 months for high-risk accounts (banking, email, company accounts).
Immediately if a security breach occurs or if the password is compromised.
Use a password manager (Bitwarden, 1Password, LastPass) to store complex passwords securely.
-
Disable LM and NTLM Hashing (For Windows Users)
Older versions of Windows used LAN Manager (LM) and NTLM hashes. Those are easily cracked using rainbow tables. If your system still stores LM hashes then it is vulnerable.
How to Disable LM and NTLM Hashing (Windows Guide):
Open Group Policy Editor (gpedit.msc).
Navigate to:
Computer Configuration → Windows Settings → Security Settings → Local Policies → Security Options
Locate “Network security: Do not store LAN Manager hash value on next password change” and set it to Enabled.
Windows 10 and later versions disable LM hashing by default, but older systems require manual configuration.
-
Encrypt Password Storage with Key Stretching
Key stretching makes hash cracking significantly harder by forcing multiple computations per password guess.
Recommended Key Stretching Techniques:
PBKDF2 – Uses multiple iterations of hashing to slow down cracking attempts.
Argon2 – The most secure option is using both time and memory-intensive operations.
Why It Works: Even if an attacker gets access to password hashes then they must perform thousands of computations per guess. That is making attacks extremely slow and costly.
-
Monitor for Data Breaches & Use Compromised Password Checkers
Attackers often use previously leaked password hashes to build more efficient rainbow tables. Regularly checking if your credentials have been leaked can prevent attacks before they happen.
How to Check if Your Passwords Are Compromised:
Use Have I Been Pwned (haveibeenpwned dot com) – Check if your email or password appears in known data breaches.
Enable real-time security alerts from password managers.
Actionable Tip: If your password is leaked then change it immediately and enable MFA.
Importance of Regularly Updating Password Security Policies
For organizations, enforcing strong password policies is crucial to prevent rainbow table attacks.
Best Practices for Companies:
Require salted password hashing across all authentication systems.
Enforce complex password creation rules for employees.
Implement role-based access control (RBAC) – Limit password exposure to authorized personnel only.
Conduct cybersecurity training – Educate employees on password security, phishing threats, and attack methods.
Why It Matters: Many security breaches happen due to weak password policies. Regularly review and update them to stay ahead of attackers.
Rainbow table attacks exploit weak password hashing to crack passwords quickly. The best defenses include:
Salting passwords and using strong hashing algorithms.
Enabling multi-factor authentication (MFA) for added security.
Using long and complex passwords to increase cracking difficulty.
Monitoring for breaches and updating passwords regularly.
Implement these security measures to significantly reduce the risk of rainbow table attacks and enhance overall cybersecurity.
Final Security Checklist: Protecting Against Rainbow Table Attacks
Hashing & Encryption
Use strong hashing algorithms like bcrypt, PBKDF2, or Argon2.
Always add salt to hashes to prevent precomputed attacks.
Consider key stretching techniques to slow down attacks.
Password Security
Enforce long and complex passwords (at least 12-16 characters).
Avoid using common or easily guessable passwords.
Implement password expiration policies and encourage regular updates.
Multi-Factor Authentication (MFA)
Enable 2FA/MFA for extra security beyond passwords.
Use authentication apps like Google Authenticator, Microsoft Authenticator, or YubiKey.
System & Network Security
Implement rate limiting and account lockout after multiple failed login attempts.
Regularly update and patch software to protect against vulnerabilities.
Use firewalls and intrusion detection systems (IDS) to monitor threats.
User Awareness & Policies
Educate employees and users about password security best practices.
Encourage the use of password managers for secure storage.
Conduct regular security audits and penetration testing.
By following this checklist, you can greatly reduce the risk of rainbow table attacks and strengthen your overall cybersecurity posture.
Limitations of Rainbow Table Attacks
Rainbow table attacks are a powerful password-cracking method. However, they have several limitations that make them ineffective in many modern security systems. Let us explore the key scenarios where rainbow tables do not work and why.
- Salted Hashes Render Rainbow Tables Useless
Why? Salting introduces a unique random value (salt) to each password before hashing. That means even identical passwords generate different hash values.
Effect: Attackers cannot precompute hashes because each user’s password hash is unique. Salting makes rainbow tables ineffective.
Example:
- Without salt: password → 5f4dcc3b5aa765d61d8327deb882cf99
- With salt (random123): passwordrandom123 → a9c9f3b6d12a73208bafefca82be093f
Since attackers do not know the salt, they cannot use precomputed rainbow tables.
- Strong Hashing Algorithms Resist Attacks
Why? Modern hashing algorithms like bcrypt, Argon2, and PBKDF2 are designed to be slow and computationally expensive. That is making precomputed attacks impractical.
Effect: Since these algorithms require significant time and computational power per hash, generating a rainbow table for them would take an unreasonable amount of time and storage.
Example:
- MD5 & SHA-1: Vulnerable to rainbow table attacks.
- bcrypt, Argon2, PBKDF2: Highly resistant to rainbow tables due to salting and key stretching.
- Large Keyspace Makes Precomputation Impractical
Why? The larger the character set and password length, the more time and storage is needed to precompute hash tables.
Effect: Generating a rainbow table for all possible 12-character passwords using uppercase, lowercase, numbers, and symbols would be impossible due to the enormous number of possibilities.
Example:
- A 6-character password (only lowercase) → Rainbow tables feasible.
- A 12-character password (upper + lower + numbers + symbols) → Storage and computation explode exponentially. That is making attacks impractical.
- Key Stretching Increases Hashing Time
Why? Key stretching forces hash computations to run multiple iterations (thousands or millions of times). Key stretching is making precomputed attacks slow and resource-intensive.
Effect: Rainbow tables rely on fast, single-iteration hash lookups. However, with key stretching, each hash computation takes longer. That is making the attack inefficient.
Example:
- A single SHA-256 hash takes milliseconds.
- A bcrypt hash (cost factor 12) takes several hundred milliseconds to seconds. That is making large-scale rainbow table attacks infeasible.
- Multi-Factor Authentication (MFA) Reduces Impact
Why? Even if an attacker cracks a password then they still need a second authentication factor (OTP, biometric, hardware key) to access the account.
Effect: Even if a rainbow table attack succeeds then the attacker cannot gain access without additional credentials.
Example:
- With MFA → Even if John123’s password is cracked, the hacker still needs his fingerprint or authentication app code.
- Rainbow Tables Only Work on Weak or Unsalted Hashes
Why? If a website or system uses properly salted, stretched, and strong hashing algorithms, precomputed attacks become impossible.
Effect: Rainbow table attacks only work if passwords are stored unsalted or in weak hashes like MD5 or SHA-1.
Example:
- A website storing unsalted MD5 hashes → Vulnerable to rainbow tables.
- A system using bcrypt + salting → Completely immune to rainbow tables.
Rainbow table attacks are becoming obsolete due to modern security practices like salting, strong hashing, key stretching, and MFA.
Attackers now favor brute-force or credential stuffing instead of rainbow tables.
Using strong passwords, MFA, and modern hashing algorithms makes rainbow table attacks ineffective.
Future of Password Security: Will Hashing Become Obsolete?
As cyber threats evolve, traditional password-based authentication methods are increasingly being questioned. While password hashing techniques like salting, peppering, and key stretching have improved security, attackers continue to develop more advanced cracking methods. This raises the question: Will password hashing become obsolete in the future?
-
The Limitations of Password-Based Security
Weak Passwords – Many users still create easy-to-guess passwords. That is making even the best hashing techniques ineffective.
Reused Credentials – Users often reuse passwords across multiple sites. It is making them vulnerable to credential-stuffing attacks.
Phishing Attacks – Even hashed passwords cannot prevent phishing, where attackers trick users into revealing credentials.
Database Breaches – If hackers steal a password database then they can attempt to crack the hashes using powerful GPUs and cloud computing.
Given these weaknesses, security experts are moving toward passwordless authentication methods to reduce reliance on passwords entirely.
-
Emerging Alternatives to Password Hashing
Biometrics: The Rise of Fingerprint and Face Recognition
Biometric authentication uses unique physical traits like fingerprints, facial recognition, or iris scans for security.
Pros:
Harder to forge or steal compared to passwords.
Eliminates the need for users to remember complex passwords.
Faster authentication process.
Cons:
Privacy concerns—biometric data leaks cannot be reset like passwords.
Not foolproof—researchers have bypassed facial recognition using deepfake AI and 3D masks.
Not universal—biometric authentication requires specific hardware.
Passwordless Authentication: One-Time Codes & Passkeys
Instead of using passwords, users authenticate via:
- Magic Links – A one-time login link sent to the user’s email.
- OTP (One-Time Passwords) – Temporary codes sent via SMS or an authenticator app.
- Passkeys – Cryptographic keys stored securely on a device (Apple’s Face ID or Google’s FIDO2 implementation).
Pros:
Eliminates the risks of weak/reused passwords.
Reduces phishing attacks—there is no password to steal.
More user-friendly and convenient.
Cons:
Device-dependent—if you lose access to your phone or email then logging in becomes difficult.
OTP interception—Attackers can hijack SMS OTPs via SIM swapping.
Multi-Factor Authentication (MFA): Strengthening Security Layers
Instead of replacing passwords entirely, many organizations add extra layers of security through MFA:
- Something You Know (Password or PIN)
- Something You Have (Authenticator app, security key, or smart card)
- Something You Are (Fingerprint or facial recognition)
Pros:
Even if a password is leaked then attackers cannot access an account without the second factor.
FIDO2-based security keys (like YubiKey) offer strong authentication without traditional passwords.
Cons:
User adoption is slow—many people find MFA annoying.
Hardware-based MFA (security keys) requires users to carry an additional device.
-
The Future: A Passwordless World?
Tech giants like Google, Apple, and Microsoft are pushing for passwordless authentication using FIDO2 and passkeys.
Many security experts believe that passwords will become a secondary or backup method, rather than the primary form of authentication.
AI-driven authentication systems may soon analyze behavior patterns (typing speed, location, and device usage) to dynamically verify identity.
Is Password Hashing Becoming Obsolete?
Not yet—password hashing is still essential for securing existing systems.
However, new authentication methods are reducing reliance on passwords. That is making attacks like rainbow table attacks and brute-force attacks less effective.
Password hashing will not disappear overnight. However, reliance on it is decreasing.
Biometrics, passkeys, and multi-factor authentication (MFA) are leading the future of secure authentication.
Organizations should adopt a hybrid approach. The hybrid approach combines password security best practices with passwordless alternatives wherever possible.
Conclusion
Rainbow table attacks are a serious cybersecurity threat. They are capable of cracking weak or unsalted password hashes within seconds. These attacks leverage precomputed hash tables to bypass traditional brute-force methods. That makes them highly efficient for hackers.
The risks associated with rainbow table attacks include:
Fast password cracking compared to brute-force methods.
Severe impact on weak hashing algorithms like MD5 and unsalted SHA-1.
Compromised user accounts leading to data breaches and identity theft.
To defend against these attacks, proactive security strategies are essential:
Use strong, salted hashing algorithms like bcrypt, PBKDF2, or Argon2.
Enable multi-factor authentication (MFA) to add an extra layer of security.
Enforce long and complex passwords to resist cracking attempts.
Regularly update passwords and security policies to stay ahead of cyber threats.
Both individuals and organizations need to implement these best practices. That can significantly reduce their vulnerability to rainbow table attacks. Cybersecurity is an ongoing effort. Staying informed and proactive is the key to safeguarding sensitive data.
FAQ on Rainbow Table Attack
What is a rainbow table attack?
A rainbow table attack is a password-cracking technique. In which hackers use precomputed hash tables to quickly break weakly hashed passwords.
How does a rainbow table attack work?
Hackers compare hashed passwords against precomputed hash tables. That allows them to crack weak passwords faster than brute-force methods.
How does salting protect against rainbow table attacks?
Salting adds a unique, random string to each password before hashing. Salting makes precomputed rainbow tables ineffective.
What is peppering, and how does it improve security?
Peppering adds a secret, system-wide key to hashes. Peppering makes it harder for attackers to crack passwords, even if they steal the hash database.
Why are MD5 and SHA-1 vulnerable to rainbow table attacks?
MD5 and SHA-1 lack built-in salting and are computationally weak. That makes them easy targets for precomputed hash attacks.
What are the best hashing algorithms to prevent rainbow table attacks?
Use bcrypt, PBKDF2, or Argon2, as they include salting, stretching, and adaptive hashing. That is making attacks impractical.
Can multi-factor authentications (MFA) prevent rainbow table attacks?
Yes! Even if a hacker cracks a password then MFA adds an extra security layer. And hacker requires a second verification step.
Are rainbow table attacks still effective today?
Rainbow tables are ineffective against properly salted hashes. However, weakly hashed passwords (like MD5) remain vulnerable.