Introduction: What is Hardcoding?
Hardcoding refers to embedding fixed values directly into the source code of a program. These values can be specific data, file paths, credentials, or other constants that the code relies on to function.
In other words, Hardcoding is one of the software development practices of embedding fixed sensitive data directly into a program. Generally, the hard-coded data can only be modified by editing the source code and recompiling again.
Hard Code includes:
- Numeric values, strings, or constants
- File Paths
- Configuration Settings
- URLs
In other words, Hard-code is nothing but writing fixed data within code that is not easily modified or reused.
Hardcoded values are static and cannot be easily changed without modifying the actual code. They are not being dynamic or flexible.
For example, in a Python program, Hard Coding could look like this:

Here, the values “admin” and “1234” are hardcoded into the program. This means if you ever need to change them, you would have to go into the code itself, find those values, and replace them. This can be fine for small programs or quick tasks. But it often creates problems in larger, more complex systems.
In software development, Hardcoding is generally considered bad practice. That is especially true when the same values are used in many places. It reduces flexibility because the code becomes harder to maintain and update.
Define Hardcoding and Provide a Basic Overview of the Term
Hardcoding is a practice where fixed values or data are directly written into a program’s source code. It is directly written instead of being stored in external files or retrieved dynamically. These values can be anything from configuration settings, file paths, database credentials, or even user-specific data.
For example, if a program needs to access a specific folder, a hardcoded approach would directly write the folder’s path into the code:
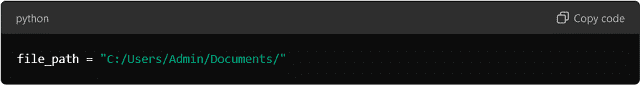 Here, the file path is hardcoded. If the file location changes the code must be manually updated. That makes it less flexible and harder to maintain. In many cases, this approach is seen as inefficient because it does not allow for adaptability.
Here, the file path is hardcoded. If the file location changes the code must be manually updated. That makes it less flexible and harder to maintain. In many cases, this approach is seen as inefficient because it does not allow for adaptability.
In normal programming practices, Hardcoding is generally avoided. That is in favor of more dynamic solutions, like using configuration files or environment variables. This makes the code easier to manage in large applications where frequent changes might occur.
Where Hardcoding is commonly seen in software development
Hardcoding is commonly seen in several areas of software development. They are often used when developers need quick solutions or when dynamic handling of data is not a priority.
Here are some common scenarios:
- Configuration Settings: Developers use sometimes hardcode settings like database connections, API keys, or file paths directly into the code. Instead of reading these from a config file, they are directly written into the program. That makes future changes more difficult.
- Testing and Prototyping: In the early stages of development, the focus is on getting something to work quickly. Therefore Hardcoding is often used. Developers might use hardcode values for testing purposes to avoid setting up a complex system early on.
- User Interfaces: Hardcoded values can also be found in the development of user interfaces. For example, default text, button labels, or styles might be directly placed into the code instead of being fetched from external files or databases.
- Embedded Systems: In some cases, Hard Coding is used in embedded systems where resources are limited and dynamic data retrieval is unnecessary. In these systems, fixed values are often included directly in the code.
- Error Messages and Logs: Hard-Coding is often used for error messages or log entries in various applications. Instead of having a centralized system for error handling, developers may write specific error text into different parts of the code.
These are common, Hardcoding in a few areas. These can lead to maintainability and scalability issues if not properly managed.
Why Hardcoding Can Be Problematic
Hardcoding might seem like a quick fix. But it often leads to significant problems in the long run.
Here are some reasons why Hardcoding can be problematic:
- Lack of Flexibility: Hardcoded values are always fixed. This means that if you need to change a value—like a file path or a password—you have to modify the code itself. In larger systems, the same value is used in multiple places. This can be tedious and error-prone. Each change requires a full code deployment. Further, that can disrupt the entire system.
- Difficult to Maintain: When Hard-Coding is used extensively maintaining the code becomes harder over time. Imagine a scenario where hardcoded values exist in different parts of the system. If you need to update one value, you may miss some places. That may lead to bugs. This increases the effort needed for debugging and updating the software.
- Scalability Issues: Hardcoding limits the scalability of a system. If your application grows and starts handling different environments (development, testing, and production), hardcoded values will need to change for each environment. A better approach is to use configuration files or environment variables that adapt automatically.
- Security Risks: Hard-Coding sensitive data like passwords, API keys, or database credentials creates a significant security risk. If this information is hardcoded, it can be easily exposed to anyone with access to the source code. This makes your system vulnerable to attacks and data breaches.
- Reduces Code Reusability: When values are hardcoded, it becomes difficult to reuse the code in different contexts. Developers would need to modify the code each time it is reused. That defeats the purpose of modularity in programming. Replacing hardcoded values with dynamic inputs increases code reuse and efficiency.
- Error-Prone Updates: Updating hardcoded values across large systems introduces a higher risk of mistakes. For example, a simple typo when changing a hardcoded URL or file path could lead to system crashes or unexpected behavior.
Avoid Hardcoding to create more adaptable, secure, and maintainable systems. It is a best practice to keep your code dynamic and flexible, using configuration files, databases, or environment variables to store changing values.
Scalability, Maintainability, and Flexibility Issues with Hardcoding
Hardcoding often leads to problems related to scalability, maintainability, and flexibility in software systems. Here is how these issues arise:
Scalability Issues
Scalability refers to how well a system can handle increasing amounts of work or expand when necessary. Hard-Coding limits scalability because fixed values cannot easily adapt to changes in the system. For example:
- If a project expands to support multiple environments (development, staging, and production), hardcoded configurations for each environment become difficult to manage.
- Large applications often need to adjust settings like database connections, URLs, or paths dynamically. Hardcoded values require manual intervention for each update. That is inefficient and prone to errors.
A scalable system should be flexible enough to change configurations or settings automatically. However, Hardcoding requires manual code changes that lead to inefficiency.
Maintainability Issues
Maintainability involves how easy it is to update and manage code over time. Hardcoding makes maintaining code more difficult because:
- Changing a hardcoded value requires modifying the source code. If the same value is used in multiple places, you need to find and update each instance. That can lead to missed changes and bugs.
- Hardcoded values often lack documentation. That makes it unclear why certain data was used for future developers who might work on the code. This makes it harder to debug or update the code.
Well-maintained code should use external configurations or parameters that can be updated without touching the core logic. But Hard-Coding violates this principle.
Flexibility Issues
Flexibility refers to the ability of a system to adapt to new requirements or changes. Hardcoded values reduce flexibility because:
- If you want to change a value (server address, API key, or feature toggle), you have to modify the code and redeploy it. This is time-consuming for large applications.
- Hardcoding does not allow for dynamic or user-driven changes. For example, hardcoded UI labels or settings make it impossible to adjust features based on user preferences or different locales.
To improve flexibility, developers often use configuration files, databases, or environment variables. That allows them to make changes without modifying the codebase directly.
Addressing scalability, maintainability, and flexibility can create more adaptable, reliable, and efficient systems. That is reducing the risks associated with Hard Coding.
Real-World Problems Caused by Hardcoding
Hardcoding has caused several significant real-world issues. That is particularly true in large-scale software systems. Here are some examples of the types of problems that can arise:
-
Security Vulnerabilities
One of the biggest risks of Hardcoding is exposing sensitive information. Hardcoding passwords, API keys, or encryption keys directly into code leaves them vulnerable to hackers. In the 2017 Equifax breach, a hardcoded admin password in their system was one of the contributing factors that allowed hackers to access sensitive data. That affected millions of users.
-
System Failures
Hardcoded values can lead to critical system failures. That is especially true when they are not updated properly. Hard Coding URLs or IP addresses for external services can cause downtime if the service location changes. A real-world incident occurred in 2019 when several applications experienced failures due to hardcoded IP addresses for Amazon Web Services (AWS). That was causing downtime when AWS updated their IP ranges.
-
Difficulty in Scaling
In large software systems, scalability is very crucial. Hardcoded values make it extremely difficult to scale systems across multiple environments or regions. For instance, a company might want to deploy the same software in multiple regions. However, hardcoded settings for database connections or file paths would require extensive changes in the code for each deployment. This lack of flexibility makes it hard to expand or adjust the system without significant manual work.
-
Expensive Maintenance
Hardcoded values can result in higher maintenance costs over time. Developers need to update these values manually. That can lead to errors or overlooked changes. That is especially true in large codebases.
This slows down development. Further, it also increases the likelihood of bugs. One example is a financial system that hardcoded tax rules into the code. When tax laws changed, the entire system needed an expensive and time-consuming overhaul to update all the hardcoded rules.
-
Incompatibility with Different Environments
Hardcoded values tied to specific environments can cause compatibility issues when moving code between development, staging, and production environments. A famous example is the healthcare.gov website. It experienced crashes and poor performance at launch partly due to hardcoded configurations that could not handle the transition between testing and real-world usage at scale.
These examples highlight how Hard Coding can introduce unnecessary risks and challenges to software development. They often result in security issues, system failures, and costly maintenance.
When is Hardcoding Acceptable?
Hardcoding is generally discouraged in software development. But, there are specific situations where it can be acceptable or even beneficial. These situations often involve simpler, smaller-scale projects or cases where dynamic handling is not necessary.
Here are a few scenarios where Hardcoding may be acceptable:
-
Prototyping or Quick Fixes
In the early stages of development like during prototyping or proof-of-concept projects, Hard Coding can save time. The goal during prototyping is often to demonstrate a concept quickly rather than building a fully dynamic solution. In these cases, developers may hardcode values to speed up the process. Prototypes are typically discarded or rewritten later. Therefore, the risks of Hardcoding are minimal.
-
Small, Single-Use Scripts
For small programs or one-time-use scripts, the values are unlikely to change. Therefore, Hardcoding can be a simple and efficient approach in those programs. For example, if a script is needed to automate a minor task that will only be run once or twice, Hardcoding values can make the code shorter and easier to write.
-
Fixed, Unchanging Values
If certain values are unlikely to ever change—such as mathematical constants (PI), default settings, or industry-standard thresholds—Hard Coding can be acceptable. These values remain constant across the lifetime of the software. So there is no need to introduce the complexity of dynamic data handling.
-
Limited-Access Systems
In some cases, systems with limited access or environments that are tightly controlled can justify Hardcoding certain values. For instance, an embedded system in a hardware device may have hardcoded configurations that do not need to be updated dynamically. That is especially when network or storage constraints make external configuration impractical.
-
Temporary Solutions
Sometimes, Hard Coding is used as a temporary workaround until a more permanent solution is implemented. For example, during an urgent bug fix, developers might hardcode values to resolve the issue quickly and plan to replace the hardcoded data with a more flexible solution later. In this case, documentation and clear plans to refactor are important to prevent the temporary Hardcoding from becoming permanent.
-
Internal or Closed Systems
In software that operates in a closed environment or is only used internally, Hard Coding certain values may not pose as many risks. If the system is not exposed to external users or environments and the hardcoded values are rarely updated, it might be acceptable to hardcode them for simplicity.
In general, Hardcoding can sometimes be useful. It is essential to weigh the benefits against the potential downsides like maintainability, scalability, and security risks. For long-term or complex projects, more dynamic approaches are typically recommended.
Scenarios Where Hardcoding Might Make Sense
Hardcoding is normally avoided in software development. However, it can be useful in certain situations where flexibility and scalability are less important. Here are some scenarios where Hard Coding might be an acceptable solution:
-
Quick Prototypes
When developing a prototype or proof of concept, the goal is to demonstrate functionality quickly. In these cases, developers often need to prioritize speed over code quality. Hard-Coding allows them to quickly insert values without spending extra time on dynamic data handling or setting up configuration files. Since prototypes are often discarded or rewritten later, the risks of Hardcoding are minimal. This approach allows developers to get feedback on the concept without being bogged down by technical details.
-
One-off Scripts
For simple, one-time-use scripts, Hardcoding can save time and effort. These are typically small programs designed to perform a specific task like data processing or file manipulation. They are not meant for long-term use. Since the script is intended to be used only once or twice, Hard-Coding values directly into the code. Hard Coding can make the process more efficient. For example, a script to batch rename files might have hardcoded file paths and names because they do not need to be reused.
-
Fixed, Unchanging Data
Sometimes, certain values in a program are fixed and unlikely to change. For example, mathematical constants (like Pi) or specific, industry-standard thresholds (regulatory limits or default color codes) can be hardcoded because they remain consistent throughout the life of the software. In such cases, Hardcoding reduces complexity since there is no need to externalize or dynamically calculate these values.
-
Embedded or Resource-Constrained Systems
In embedded systems or devices with limited resources, Hard-Coding can be necessary due to constraints like limited memory or processing power. For instance, small devices like IoT sensors might hardcode configurations because setting up external configurations is impractical in these environments. These systems are often designed for a specific purpose. The hardcoded values are tightly aligned with that purpose.
-
Internal or Closed Systems
Hardcoding may also make sense in internal systems where the software is used by a limited group of people. It is not exposed to external users or environments. In these cases, the values being hardcoded are unlikely to change frequently. Further, the risks of security vulnerabilities or maintenance issues are lower.
-
Temporary Solutions or Quick Fixes
When dealing with an urgent issue or bug, developers sometimes use Hardcoding as a temporary solution. For example, if a particular feature is breaking due to a misconfigured setting, Hard-Coding the correct value may be a fast way to resolve the issue. However, this should be seen as a temporary workaround. The developer should have plans to refactor the code later and replace the hardcoded value with a more flexible approach.
Hardcoding is generally discouraged for long-term projects. But, it can be useful in situations that require speed, and simplicity, or when the data is unlikely to change. For quick prototypes, one-off scripts, and environments with limited resources, Hardcoding can provide a practical, short-term solution. However, developers should always weigh the benefits against future maintenance and scalability challenges.
Examples of Hardcoding in Programming
Hardcoding can be seen across different types of programming tasks and environments. Here are some examples of Hard-Coding in various programming contexts:
-
Hardcoding Values in Code
A common example is embedding fixed values directly into the code like file paths, database credentials, or configurations.
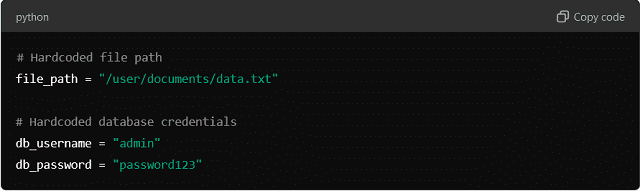 In this case, the values are static and fixed. That means any change to the file path or database login would require modifying the code and redeploying the software.
In this case, the values are static and fixed. That means any change to the file path or database login would require modifying the code and redeploying the software.
-
Hardcoded URLs and Endpoints
Another typical case is Hardcoding URLs or API endpoints. That can cause significant issues if the URL changes.
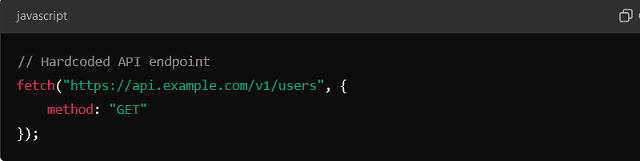 If the API version is updated or the service changes domains, the code will break unless the hardcoded URL is updated.
If the API version is updated or the service changes domains, the code will break unless the hardcoded URL is updated.
-
Hardcoding HTML or UI Elements
In web development, Hardcoding text or styles in HTML or CSS is a common example. Instead of using variables or external resources, values are written directly into the code. That makes it difficult to adapt the website to different users or languages.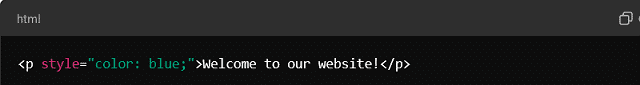
Here, the color “blue” is hardcoded. If the style needs to change dynamically, it would require rewriting this part of the HTML or CSS.
-
Hardcoding Logic in Functions
Hardcoding logic in functions can limit the flexibility of the software. For example, Hard-Coding a specific discount percentage directly into the function:
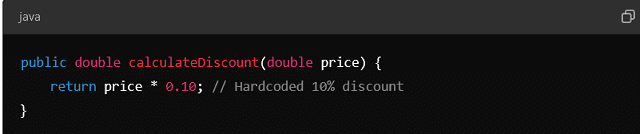
If the discount needs to be updated or made configurable, the hardcoded value would need to be changed directly in the code.
-
Hardcoding Credentials or API Keys
One of the most dangerous forms of Hard-Coding is embedding sensitive information like API keys, database credentials, or encryption keys in the source code.
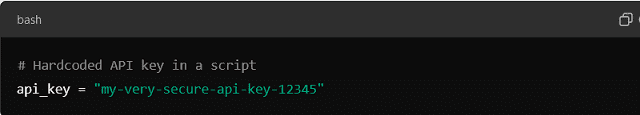
This introduces serious security risks. That is especially true if the code is shared or pushed to a public repository. Attackers can easily exploit this information to gain unauthorized access to the system.
-
Hardcoding in Embedded Systems
In embedded systems, Hardcoding can be necessary due to the limited resources of the device. For example, firmware on microcontrollers might have hardcoded values for sensors or communication protocols.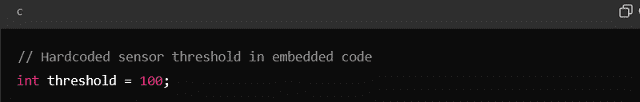
In this case, the threshold value is fixed and might be hard to change once the device is deployed.
-
Hard Coding Language or Locale Settings
In applications that support multiple languages or regions, Hardcoding text or language settings can cause problems with localization.
This approach makes it difficult to support different languages without rewriting parts of the code.
These examples highlight the various ways Hard-Coding can be used in programming. It might simplify certain situations. But, it also introduces challenges related to scalability, flexibility, and security. Developers need to be cautious and only use Hardcoding in scenarios where it makes sense like temporary fixes or single-use scripts.
Simple Code Examples in Languages like Python, Java, or JavaScript
Hardcoding values directly into code can be illustrated with simple examples in Python, Java, and JavaScript. These examples show how values like paths, configurations, and credentials are embedded in the code.
Python Example
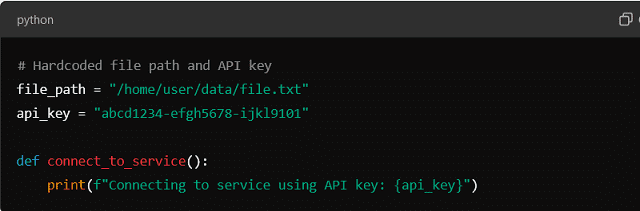 In this Python example, both the file path and API key are hardcoded. This can be convenient when developing quickly. However, changing the file location or API key later will require directly modifying the code.
In this Python example, both the file path and API key are hardcoded. This can be convenient when developing quickly. However, changing the file location or API key later will require directly modifying the code.
Java Example
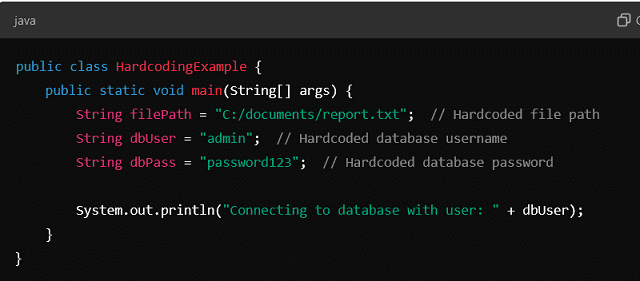 In this Java example, the file path and database credentials are hardcoded. That can be convenient during development. However, if the credentials change, the source code must be updated. And that could lead to security issues.
In this Java example, the file path and database credentials are hardcoded. That can be convenient during development. However, if the credentials change, the source code must be updated. And that could lead to security issues.
JavaScript Example
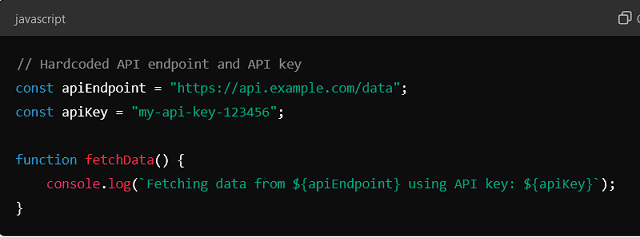 Here, the API endpoint and key are hardcoded into the JavaScript function. That makes it easy to use. However, it limits flexibility if the API endpoint or key changes.
Here, the API endpoint and key are hardcoded into the JavaScript function. That makes it easy to use. However, it limits flexibility if the API endpoint or key changes.
Show How Hardcoding can be both Convenient and Limiting
Convenience of Hard Coding
- Faster Development: Hard Coding allows developers to quickly get a feature or prototype up and running without setting up external configuration files or environment variables.
- Simplifies Small Projects: For small, one-off scripts or quick fixes, Hardcoding saves time and effort. It eliminates the need to set up additional infrastructure like configuration management systems.
Example: Hardcoding a file path in a small data processing script simplifies the task, as seen in this Python code:
 For small, temporary projects, Hard-Coding the file path works perfectly.
For small, temporary projects, Hard-Coding the file path works perfectly.
Limitations of Hardcoding
- Lack of Flexibility: When values are hardcoded, it becomes difficult to adapt the code to different environments or configurations. For instance, moving the above script to another machine would require changing the hardcoded file path. That may lead to errors if forgotten.
- Maintenance Issues: If changes need to be made (updating an API key or database credentials), every instance of the hardcoded value must be located and modified. Missing any of the changes increases the risk of bugs.
Example: Consider this JavaScript snippet:
- If the API URL changes, every piece of code that references apiUrl must be updated. This can become cumbersome in large projects.
- Security Risks: Hardcoding sensitive information like credentials or API keys can expose the software to security vulnerabilities. That is especially true in open-source projects. Attackers can easily extract these values from the source code.
Hardcoding can simplify development and speed up prototyping. But it can also introduce issues related to flexibility, scalability, and security. That particularly happens in larger projects or long-term maintenance. Using configuration files, environment variables, or databases to store values instead of Hard Coding is often a better approach for complex systems.
Best Practices to Avoid Hardcoding
Hardcoding values in code can lead to issues like poor scalability, inflexibility, and maintenance challenges. Following best practices can help developers avoid these pitfalls. Below are some strategies and coding standards to replace Hard Coding and ensure clean, maintainable code.
-
Use Configuration Files
Configuration files allow values such as file paths, API keys, and database credentials to be stored outside of the main codebase. This ensures that changes can be made without altering the core code. Common formats for configuration files include:
- JSON: A lightweight format widely used for configuration purposes.
- YAML: A human-readable format that is popular for storing configuration settings.
- INI/XML: Older formats are still in use for various systems.
Example (Using JSON as a config file in Python):
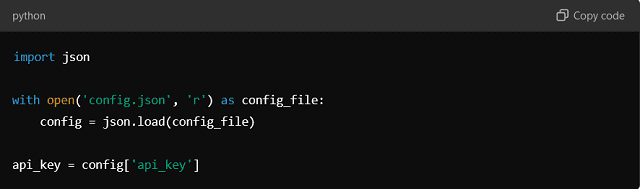
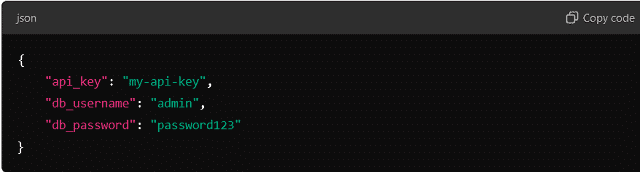 Then, load the configuration in code:
Then, load the configuration in code:
Benefits:
- Configuration changes do not require code modification.
- Easier to manage for different environments (development, testing, production).
-
Environment Variables
Environment variables are another alternative to Hard Coding. That is the best fit for sensitive information like passwords, API keys, and credentials. They provide a secure way to manage configurations that vary between different environments.
Example (In Python):
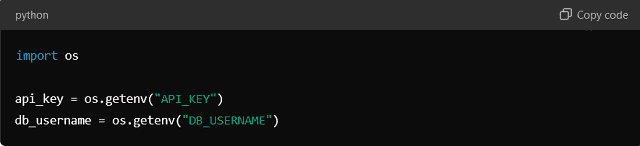
Benefits:
- Keeps sensitive information out of the source code.
- Ideal for managing configurations across various deployment environments (development, staging, production).
- Can be used in containerized environments (Docker) and CI/CD pipelines.
-
Databases for Dynamic Values
For applications that require frequent updates or dynamic values (feature toggles, pricing), storing values in a database is a more flexible option than Hard Coding.
Example: Instead of Hard Coding discount percentages, a database table can be used:
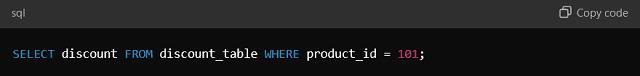
Benefits:
- Centralized storage of data that can be updated without code changes.
- Enables dynamic updates without redeploying code.
-
Use Dependency Injection
Dependency Injection (DI) helps in passing dependencies (like configuration settings) into objects at runtime, instead of Hardcoding them. This makes it easier to change the configuration without altering the code.
Example (In Java using Spring Framework):

This fetches values from an external configuration. It ensures that the hardcoded value is avoided.
Benefits:
- Promotes code reusability and flexibility.
- Allows for easier testing by providing mock dependencies.
-
Coding Standards to Avoid Hardcoding
Establishing coding standards helps ensure that developers avoid Hardcoding practices. These include:
- Use Constants: Store frequently used values in constants or enums rather than Hardcoding them multiple times.
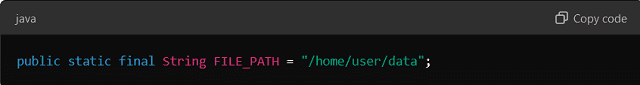
- Adopt Design Patterns: Use design patterns like Factory Patterns or Strategy Patterns to reduce the Hard-Coding of logic and make code more maintainable.
- Code Reviews: Encourage code reviews to spot instances of Hard Coding and discuss alternatives.
- DRY Principle (Do not Repeat Yourself): Hardcoded values often repeat across different files. Following the DRY principle helps developers centralize configurations. It ensures that updates are made in one place only.
Benefits:
- Promotes consistency in code.
- Reduces the chances of bugs introduced by hardcoded values.
- Ensures better security and scalability.
Following these best practices can help developers avoid Hard-Coding in their projects. Further, it ensures that the software is more scalable, maintainable, and adaptable to future changes.
Coding Standards to Help Developers Avoid Hardcoding
Adopting certain coding standards and best practices ensures that developers avoid the pitfalls of Hardcoding. Following coding standards makes code more maintainable, scalable, and adaptable.
-
Use Constants and Enumerations
Instead of embedding magic numbers or hardcoded strings in the code, define constants or use enumerations. This makes the code easier to update and more readable.
Example (In Java):
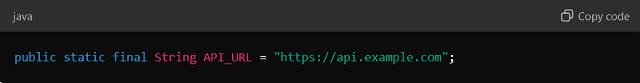 By defining constants, updates to the API URL are made in one location rather than throughout the codebase.
By defining constants, updates to the API URL are made in one location rather than throughout the codebase.
Benefits:
- Improves readability.
- Reduces the risk of errors when values need to be updated.
- Encourages consistency.
-
Externalize Configurations
Store configuration data like API keys, database credentials, and file paths in external files (.env, .json, .yaml, .ini). This allows the code to adapt to different environments without changes.
Example:
- In Python, use a .env file to store environment-specific variables and load them using a library like python-dotenv.
- In Java, use properties files or Spring Boot’s application properties.
Benefits:
- Keeps sensitive data out of source code.
- Enables different configurations for development, testing, and production environments.
-
Follow the DRY (Don’t Repeat Yourself) Principle
Hardcoding often leads to duplication, especially when the same value is used in multiple places. The DRY principle encourages storing values centrally and reusing them, rather than repeating them across the codebase.
Example: If a file path or API endpoint is used multiple times, store it in a single constant or configuration file. And refer to it in the code.
Benefits:
- Reduces redundancy.
- Simplifies updates and maintenance.
- Prevents bugs due to inconsistencies.
-
Adopt Dependency Injection (DI)
Use dependency injection frameworks to pass configuration settings or dependencies into objects. This avoids Hard Coding dependencies within classes and makes the code more modular and testable.
Example (In Java with Spring):

This approach pulls the value from a properties file rather than Hard Coding it.
Benefits:
- Improves code flexibility.
- Makes unit testing easier by allowing mock objects to be injected.
- Separates configuration from the code logic.
-
Use Design Patterns
Design patterns such as the Strategy Pattern or Factory Pattern promote flexible code that adapts to different use cases. This helps the developer to avoid the need for hardcoded logic.
- Strategy Pattern: Allows you to select algorithms at runtime without modifying the source code.
- Factory Pattern: Avoids Hard-Coding object creation logic. That makes the code more adaptable.
Benefits:
- Promotes scalability.
- Encourages code reuse.
- Makes future modifications easier without breaking existing functionality.
-
Conduct Code Reviews
Regular code reviews help catch Hard Coding issues early. Team members can discuss alternatives like using environment variables or configuration files, to eliminate Hard Coding.
Benefits:
- Encourages best practices.
- Reduces technical debt by spotting potential issues before deployment.
- Promotes collective code ownership and learning.
-
Follow Environment-Specific Configuration Standards
In complex applications, configurations may vary between environments (development, testing, and production). Adhere to standards such as the 12-Factor App. So that developers can avoid Hard-Coding environment-specific values.
Key Practices:
- Store configuration in environment variables.
- Avoid environment-specific Hard-Coding in the Codebase.
Benefits:
- Seamless transitions between environments.
- Easier deployment and configuration management.
Adhere to these coding standards. So that, developers can create code that is more maintainable, adaptable, and secure. Hard Coding is often a symptom of rushed development. But with these best practices, developers can create robust and scalable applications.
Refactoring Hardcoded Code: A Step-by-Step Guide
Refactoring hardcoded code involves systematically replacing embedded values, like strings or numbers, with more flexible solutions. This not only enhances maintainability but also makes the code easier to scale and adapt to changing requirements.
Here is a step-by-step guide to refactoring hardcoded code:
Step 1: Identify Hardcoded Values
Before refactoring, you need to locate where hardcoded values exist in your code. These could be file paths, credentials, configuration settings, URLs, or any other hardcoded constants.
Common Examples:
- API keys
- Database credentials
- URLs or file paths
- Magic numbers (numbers used without explanation)
Action:
- Search through the code for values that are directly written into the logic.
- Identify patterns where these values are used in multiple places.
Step 2: Classify the Values
Once you have identified the hardcoded values, classify them based on their nature. Decide if they should be moved to configuration files, constants, environment variables, or databases. This decision depends on the purpose and how frequently these values might change.
Types of Values:
- Sensitive values: Like API keys and passwords, move these to environment variables.
- Configurable parameters: Values that might change between environments (like database credentials). And move them to configuration files.
- Constants: Frequently used but static values (like fixed limits) should be moved to constants.
Step 3: Replace Hardcoded Values with Constants or Variables
Start by replacing hardcoded values with constants or variables. This ensures that changes can be made in one place and are reflected throughout the code.
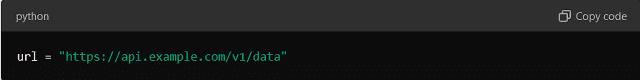
Example:
Let us say you have a hardcoded API URL in your code:
Refactor: Move this to a constant:
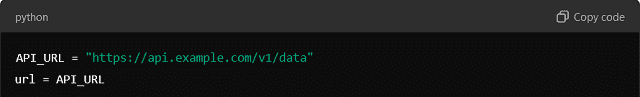
Benefits:
- Makes future changes to the URL easier.
- Improves readability by using a descriptive name.
Step 4: Use Configuration Files
For values that differ between environments (like development and production), configuration files provide flexibility. Tools like JSON, YAML, and INI files can store settings externally. That makes it easy to modify configurations without touching the code.
Example (Using a JSON configuration file in Python):
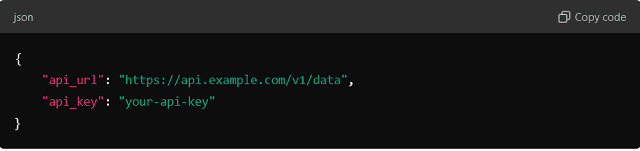
In your code, load the configuration:
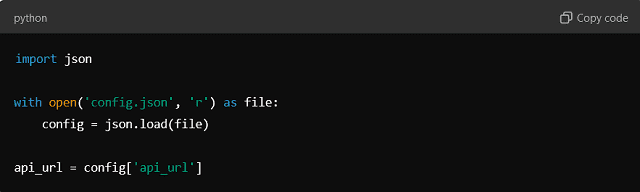
Benefits:
- Keeps code clean and decoupled from changing values.
- Allows environment-specific settings (different API URLs for staging and production).
Step 5: Leverage Environment Variables
For sensitive information like passwords or API keys, environment variables are ideal because they are not stored directly in the code. That improves security.
Example: In Python, you can load environment variables using the os module:

Benefits:
- Enhances security by preventing sensitive information from being hardcoded in the codebase.
- Easily configurable for different deployment environments (development, production).
Step 6: Refactor Repeated Hardcoded Logic with Functions
If you see repeated logic or patterns involving hardcoded values, encapsulate these in functions or methods. This reduces redundancy and makes future changes easier.
Example (JavaScript): Before refactoring:
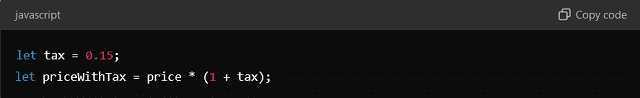
Benefits:
- Makes the code more flexible and reusable.
- Reduces repetition and keeps logic clean.
Step 7: Test Your Changes
After refactoring the hardcoded values, thoroughly test your changes to ensure that nothing breaks. This is critical when dealing with sensitive values like API keys or configuration settings, as incorrect setups can lead to failures.
- Unit tests: Check the logic that uses the replaced values.
- Integration tests: Ensure that external dependencies like APIs or databases work correctly with the new configuration.
Step 8: Document the Refactor
Document the changes made during the refactor so other developers understand the new approach. Specify where configuration files are located. Further, specify how environment variables should be set, and any other relevant information.
Example:
- Add a section in the README file detailing how to configure the application.
- Mention the location of configuration files or how to set up environment variables.
Refactoring hardcoded values enhances code flexibility, security, and maintainability. Follow these steps—identify hardcoded values, classify them, and replace them with constants or external files. Once done, test the refacto so that you can create a more adaptable and future-proof codebase.
Impact of Hardcoding on Software Security
Hardcoding is often used to simplify coding during development. However, it poses significant security risks when it comes to software applications. Here is how Hardcoding can negatively impact software security:
-
Exposure of Sensitive Data
Hard Coding sensitive information like API keys, passwords, and encryption keys directly in the source code is one of the most severe security risks. If the source code is ever leaked, attackers can easily extract this information and exploit it.
- Example: In 2014, the infamous breach of AWS credentials hardcoded into a code repository led to unauthorized access to resources. That resulted in massive data leaks.
Consequences:
- Compromised systems and data breaches.
- Exposure of private user data. That can lead to legal and compliance issues (violations of GDPR).
-
Vulnerability to Code Leaks
Even if the code is not public, internal breaches can occur. Developers may inadvertently upload hardcoded credentials to public repositories (GitHub), or they may be exposed through malicious insiders. This makes the system vulnerable to unauthorized access.
- Example: Many companies have had security issues due to developers accidentally pushing sensitive code to public repositories. At where it can be scanned and exploited.
Consequences:
- Unauthorized access to internal systems.
- Risk of exploitation by cybercriminals scanning public repositories for exposed credentials.
-
Lack of Flexibility in Security Patches
Hardcoded security configurations, like encryption algorithms or certificate paths, are difficult to update. When vulnerabilities such as weak encryption algorithms are discovered, it becomes harder to issue security patches quickly if these are hardcoded in the system.
Consequences:
- Delayed security patches, leaving the system vulnerable to known exploits.
- Increased difficulty in responding to zero-day vulnerabilities.
-
Increased Attack Surface
Hardcoded values limit the flexibility of the software. That is often increasing the attack surface. Attackers may exploit these static configurations. The hackers know that those data cannot easily be changed. For instance, if default hardcoded credentials are used, attackers could potentially gain unauthorized access by targeting these static credentials.
Consequences:
- Easier exploitation by attackers who identify default or known credentials.
- Limited defense against attacks targeting specific configurations.
-
Non-compliance with Security Standards
Most security standards and best practices like OWASP (Open Web Application Security Project) and ISO 27001, discourage the practice of Hardcoding sensitive information. Non-compliance with these standards can fail to pass security audits and may expose organizations to regulatory penalties.
Consequences:
- Failure to comply with security frameworks like OWASP Top 10.
- Fines or penalties for non-compliance with data protection regulations.
-
Difficulty in Scaling Security
Hardcoding values can make it difficult to scale security measures across multiple environments. For example, hardcoded encryption keys or API endpoints may work in a development environment but pose risks in production due to their immutability.
Consequences:
- Inability to manage security settings across multiple environments.
- Increased risk of human error when scaling or migrating applications.
Hard Coding creates critical security vulnerabilities by exposing sensitive information. It increases the likelihood of breaches. And that makes it difficult to scale and update security protocols. To avoid these risks, developers should rely on safer alternatives like environment variables, secure configuration files, or secret management tools. These practices not only protect sensitive data but also ensure compliance with security standards and help maintain a robust defense against cyber threats.
How Hardcoding sensitive information can lead to security vulnerabilities
Hardcoding is adding sensitive information like passwords or API keys directly into the source code. That poses a major security risk that can lead to significant vulnerabilities. Here is how it impacts software security:
-
Exposure of Credentials
When passwords or API keys are hardcoded in the source code, they become easily accessible to anyone who gains access to the codebase. This could happen via code leaks, insider threats, or developers unintentionally pushing sensitive code to public repositories like GitHub. Once exposed, attackers can use these credentials to gain unauthorized access to systems and data.
Example: If an API key for a cloud service is hardcoded into a publicly accessible code repository, attackers can use it to access, modify, or delete cloud resources.
Impact:
- Loss of sensitive data.
- Unauthorized access to services and databases.
- Potential for large-scale data breaches.
-
Difficulty in Rotating Keys and Passwords
Hard Coding sensitive values makes it difficult to rotate or update passwords, API keys, or tokens. That is especially true if these values are scattered throughout the code. If the credentials need to be changed, developers must manually update the code. That is not only time-consuming but prone to human error. This process delays response time in the event of a breach.
Impact:
- Delayed mitigation in case of compromised credentials.
- Higher risk of outdated or weak credentials remaining in use.
-
Vulnerability to Reverse Engineering
In compiled applications, hardcoded passwords and API keys can still be extracted by attackers through reverse engineering techniques. For instance, even if an application is built for a mobile platform, tools like APK decompilers or binary analysis tools can expose hardcoded sensitive information.
Impact:
- Increased risk of attackers gaining access to hardcoded secrets through reverse engineering.
- Breach of services and systems relying on those keys or passwords.
-
Non-compliance with Security Standards
Hard Coding sensitive data violates many industry security standards like the OWASP Top 10 and ISO 27001. These guidelines strongly recommend using secure mechanisms like environment variables, secure vaults, or configuration management tools to store sensitive information securely.
Impact:
- Failure to comply with regulatory standards.
- Penalties or legal consequences due to security breaches or non-compliance.
-
No Control over Environment-Specific Secrets
In environments like development, staging, or production, the same hardcoded API key or password might be used across all of them. If one environment is compromised, attackers can access sensitive resources across all environments.
Impact:
- Increased attack surface.
- Loss of control over environment-specific security configurations.
Safer Alternatives to Hard Coding
- Environment Variables: Store passwords or API keys in environment variables that are not committed to the codebase.
- Secret Management Tools: Use tools like AWS Secrets Manager, HashiCorp Vault, or Azure Key Vault to securely store and manage sensitive information.
- Configuration Files: Keep sensitive data in configuration files that are encrypted and excluded from version control systems.
Avoiding Hard-Coding sensitive data and using secure storage alternatives can significantly reduce the risk of unauthorized access and data breaches.
Tools and Resources to Detect Hardcoding
Detecting Hardcoding in software is critical to identifying potential vulnerabilities. That is especially true when sensitive data like passwords or API keys are hardcoded into the codebase. Various tools and resources are designed to scan, detect, and help mitigate these issues. Here are some of the most effective tools:
-
Static Code Analysis Tools
Static analysis tools can analyze the source code to detect hardcoded credentials, API keys, and other sensitive information. These tools automatically scan for patterns that suggest Hard Coding.
- SonarQube: A widely-used tool for static code analysis, SonarQube checks for various security vulnerabilities. That includes hardcoded secrets like passwords or tokens.
- Semgrep: It is a fast and customizable tool for scanning codebases. Semgrep can detect hardcoded strings and secrets by searching for specific patterns in your code.
- Checkmarx: Another powerful static analysis tool, Checkmarx is designed to detect Hardcoding and other security issues in software development.
-
Secrets Scanning Tools
These tools specifically scan repositories and code for hardcoded secrets like API keys, passwords, and private tokens. They ensure sensitive data is not accidentally exposed.
- GitGuardian: A secrets detection platform designed to scan repositories in real time for hardcoded credentials. GitGuardian is popular for both open-source and enterprise-level projects.
- TruffleHog: It is a tool that scans Git repositories for secrets. TruffleHog searches for high-entropy strings. Those are often indicative of hardcoded sensitive data like passwords or API keys.
- Gitleaks: It is a simple, fast tool to scan Git repositories for hardcoded secrets. Gitleaks is highly configurable and frequently used in CI pipelines.
-
Environment Variable and Configuration Management Tools
These tools help manage sensitive information securely. That is reducing the chances of Hardcoding sensitive values in the first place.
- Vault by HashiCorp: Vault is a tool for securely managing sensitive information like passwords, API keys, and tokens. It provides a centralized place to store secrets and access them via environment variables instead of Hard Coding them in code.
- AWS Secrets Manager: Amazon’s solution for securely managing secrets like database credentials and API keys. AWS Secrets Manager integrates with applications to dynamically retrieve credentials at runtime.
-
Code Review Tools
Code review processes can help detect Hard Coding issues early in the development cycle. These tools assist in automating and streamlining the review process.
- Reviewable: A code review platform that integrates with repositories. Reviewable helps teams spot and discuss code issues. That includes the Hardcoding of sensitive information.
- Crucible: It is developed by Atlassian. Crucible allows for collaborative code review and can be configured to flag hardcoded secrets.
-
Manual Code Auditing
While automated tools are valuable, manual code auditing is essential for detecting subtle Hardcoding issues that tools may miss. Regular audits by experienced developers or security teams can catch hardcoded credentials or configurations.
- Custom Scripts: Developers can write custom scripts to search for specific patterns of Hard Coding within Codebase like checking for strings in configuration files.
By using a combination of these tools and enforcing best practices in configuration management, you can significantly reduce the risk of hardcoded sensitive data and enhance the security of your software applications.
Hardcoding vs. Softcoding
Here is a comparison of Hard Coding vs. Soft coding in a table format:
| Aspect |
Hardcoding |
Softcoding |
Definition |
Directly embedding values in the code. | Using external sources like configuration files or databases to manage values. |
Flexibility |
Limited; changes require code modifications. | High; changes can be made without modifying the code. |
Scalability |
Difficult to scale, as updating values requires modifying multiple code instances. | Easily scalable by updating external configurations. |
Maintenance |
High maintenance, as updates require code changes and re-deployment. | Low maintenance, as values can be updated externally. |
Security |
Risky, especially if sensitive data like passwords are hardcoded. | More secure since sensitive data can be managed securely outside the code. |
Best Use Cases |
Quick prototypes, small scripts, or one-off tasks. | Applications requiring frequent updates or configuration changes. |
Impact on Performance |
Minimal, as values are directly accessed from the code. | Slight performance overhead due to accessing external sources, but generally negligible. |
Customization |
Hard to customize, and requires changing and recompiling code. | Easy to customize without touching the source code. |
Examples |
Hardcoded API keys, URLs, or credentials in a program. | Using environment variables or a config file to manage API keys or database connections. |
This comparison highlights the key differences between Hard-Coding and Soft-Coding. Further, it is showing that softcoding generally offers more flexibility, security, and maintainability, whereas Hardcoding may be useful for quick tasks but poses significant long-term challenges.
Conclusion: The Importance of Flexible Code
Writing flexible, adaptable code is essential in modern software development. Hardcoding values may seem convenient for quick fixes or prototypes, but it creates long-term issues in terms of maintainability, scalability, and security. In contrast, softcoding—using configuration files, environment variables, or databases—allows developers to update and manage data externally without changing the core codebase.
Flexible code is easier to modify. That is less error-prone and better equipped to handle future changes or scale as the project grows. Moreover, separating sensitive information from the code reduces the risk of security vulnerabilities. Those further enhance the overall robustness of the system.
Adopting coding standards that avoid Hardcoding helps ensure that software is both resilient and adaptable to evolving needs. Ultimately, prioritizing flexibility in code design leads to more efficient development cycles. Further, that lower maintenance costs, and better security.
Summary of Main Points
- Definition of Hardcoding and Softcoding: Hardcoding involves embedding fixed values directly in the code. Whereas, softcoding uses external sources like configuration files to manage values.
- Flexibility and Scalability: Softcoding allows for easier updates and scalability. The changes can be made without modifying the codebase. This is particularly important in rapidly evolving projects.
- Maintenance and Security: Hardcoded values lead to higher maintenance costs and increased security risks. That is especially true when sensitive information is involved. Softcoding mitigates these risks by managing sensitive data externally.
- Best Use Cases: Hardcoding may be acceptable in quick prototypes or small scripts. However, softcoding is essential for larger applications requiring frequent updates and flexibility.
- Tools for Detection: Various tools are available to detect Hardcoding issues. Those include static code analysis tools and secrets scanning tools. These help to maintain security standards.
Encouragement for Best Coding Practices
To ensure that your code is flexible and maintainable, consider adopting the following best practices:
- Use Softcoding Techniques: Always aim to externalize configurations and sensitive information. Employ tools like environment variables or configuration management systems.
- Implement Coding Standards: Establish coding guidelines that discourage Hardcoding and promote the use of softcoded values.
- Regularly Audit Code: Use static analysis and secrets scanning tools to regularly check for Hardcoding issues. That can ensure compliance with security best practices.
- Collaborative Code Reviews: Engage in thorough code reviews to identify potential Hard Coding instances and discuss alternatives as a team.
- Invest in Training: Educate developers about the risks of Hardcoding and the benefits of flexible coding practices.
Embrace these practices to create software that is not only easier to maintain and scale but also more secure and resilient to change. For more insights into best coding practices, consider exploring resources like the OWASP Top Ten project and Clean Code by Robert C. Martin, which emphasize security and code quality.
Frequently Asked Questions:
-
What is Hardcoding in programming?
Hard Coding is the practice of embedding fixed values directly into the source code of a program. This means that certain data such as configuration settings, URLs, or API keys, are written into the code itself rather than being stored externally. This can lead to challenges in maintaining and updating the software over time.
-
Why is Hardcoding considered a bad practice?
Hardcoding can make code less flexible. It is harder to maintain, and more prone to errors. When values are hardcoded, any change requires modifying the source code and redeploying the application. That can increase development time and introduce bugs. Additionally, hardcoded sensitive information like passwords or API keys, can pose significant security risks if exposed.
-
When might Hardcoding be acceptable?
Hardcoding is generally discouraged. But, it may be acceptable in certain situations like quick prototypes, one-off scripts, or small applications where the values are unlikely to change. In these cases, the benefits of speed and simplicity may outweigh the drawbacks of Hard-Coding.
-
What are some best practices to avoid Hardcoding?
To avoid Hardcoding, consider the following best practices:
- Use configuration files or environment variables to manage values externally.
- Implement coding standards that encourage developers to avoid Hard-Coding.
- Regularly audit your code for hardcoded values using static analysis tools.
- Engage in collaborative code reviews to identify and discuss potential Hardcoding issues.
-
How can I detect hardcoded values in my code?
Several tools can help detect hardcoded values.
That includes:
- SonarQube: Analyzes code for security vulnerabilities, including hardcoded credentials.
- Semgrep: Searches for specific patterns in code to identify hardcoded secrets.
- GitGuardian and TruffleHog: Tools specifically designed to scan repositories for hardcoded secrets like API keys and passwords.
-
What impact does Hardcoding have on software security?
Hardcoding sensitive information can lead to severe security vulnerabilities. If hardcoded passwords or API keys are exposed (through public code repositories) attackers can gain unauthorized access to systems or data. This is why it is crucial to manage sensitive data securely. Always, use environment variables or secret management tools instead of Hard Coding them.
-
Can hardcoded values affect application performance?
Hardcoded values can have minimal impact on performance compared to dynamically loaded values. But, the real concern lies in maintainability and security. Hardcoding may lead to performance issues if changes to hardcoded values necessitate extensive code modifications and testing. Those potentially cause delays and complications in the development cycle.
For further reading, consider checking sources like OWASP for security practices or Clean Code by Robert C. Martin for coding standards.







